The daily mixed spam run has just started again, these samples seen todays: “You’ve received a new fax” But the
Continue reading

The daily mixed spam run has just started again, these samples seen todays: “You’ve received a new fax” But the
Continue reading
We have added new feature for Mobile security, Contact backup and Restore. Using this feature, you can take your mobile contacts
Continue reading
Email pretending to be a Payment Reminder for Outdated Invoice from Sage Account and Payroll is being sent by Hackers. This
Continue reading
HSBC Payment Advice Issued email pretending to come from HSBC Bank UK is from a current malware BOT Family. This
Continue reading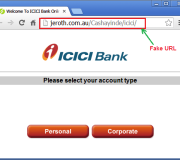
Phishing email from ICICI Bank, asking to update their Net banking Details. Beware of such fake emails. Do not get
Continue reading
Download : Corporate Edition EndPoint Security PDF
Continue reading
Many users receiving Reserve Bank of India (RBI) fake emails regarding UK Lottery. They are asking you to fill your personal details
Continue reading
Security Tip: Do not enter or use your email password on any other Site other than the actual email site.
Continue reading
I’m sure that at some point you have listened to the radio. A signal goes out and all radios in
Continue reading
Installing an application on an iPhone is a bit different than installing an application on an Android based system. With
Continue reading