The GandCrab V4 Ransomware was released with numerous changes. These changes include a different encryption algorithms, a new .KRAB extension, a new ransom note name, and a new TOR payment site.
Unfortunately, at this time, victims of GandCrab v4 cannot decrypt their files for free. GandCrab v4 distributed via fake crack sites. According to a malware analyst, one of the methods GandCrab v4 is being distributed is through fake software crack sites. The ransomware distributors will hack legitimate sites and setup fake blogs that offer software crack downloads. When a user downloads and runs these cracks, they will install the GandCrab Ransomware onto the computer.
You can see an example of one of these fake crack blogs below.
GandCrab begins using the Salsa20 encryption algorithm
The GandCrab authors love to send shout outs to various researchers, companies, and sites and with this change in their algorithm.
How GandCrab encrypts a computer?
When GandCrab is executed it will scan the computer and any network shares for files to encrypt. When scanning for network shares, it will enumerate all shares on the network and not just mapped drives.
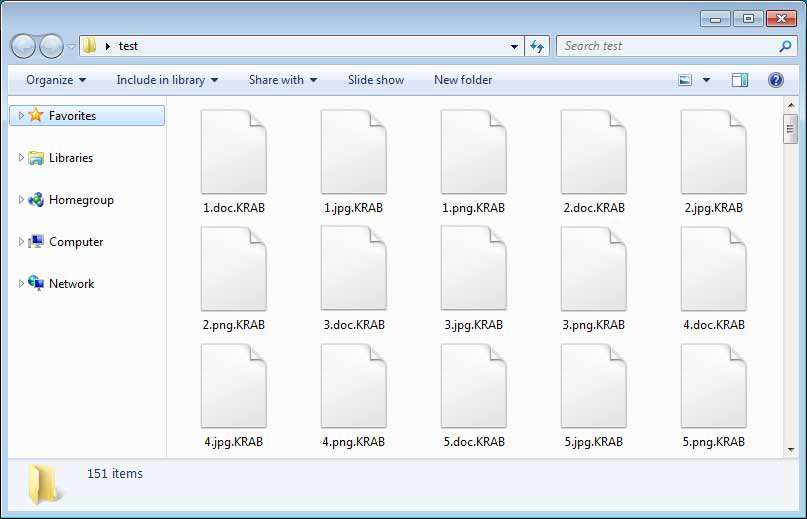
When it encounters a targeted file, it will encrypt the file and then append the .KRAB extension to the encrypted file’s name. For example, test.doc would be encrypted and renamed to test.doc.KRAB.
You can see an example of a folder with encrypted .KRAB files below.
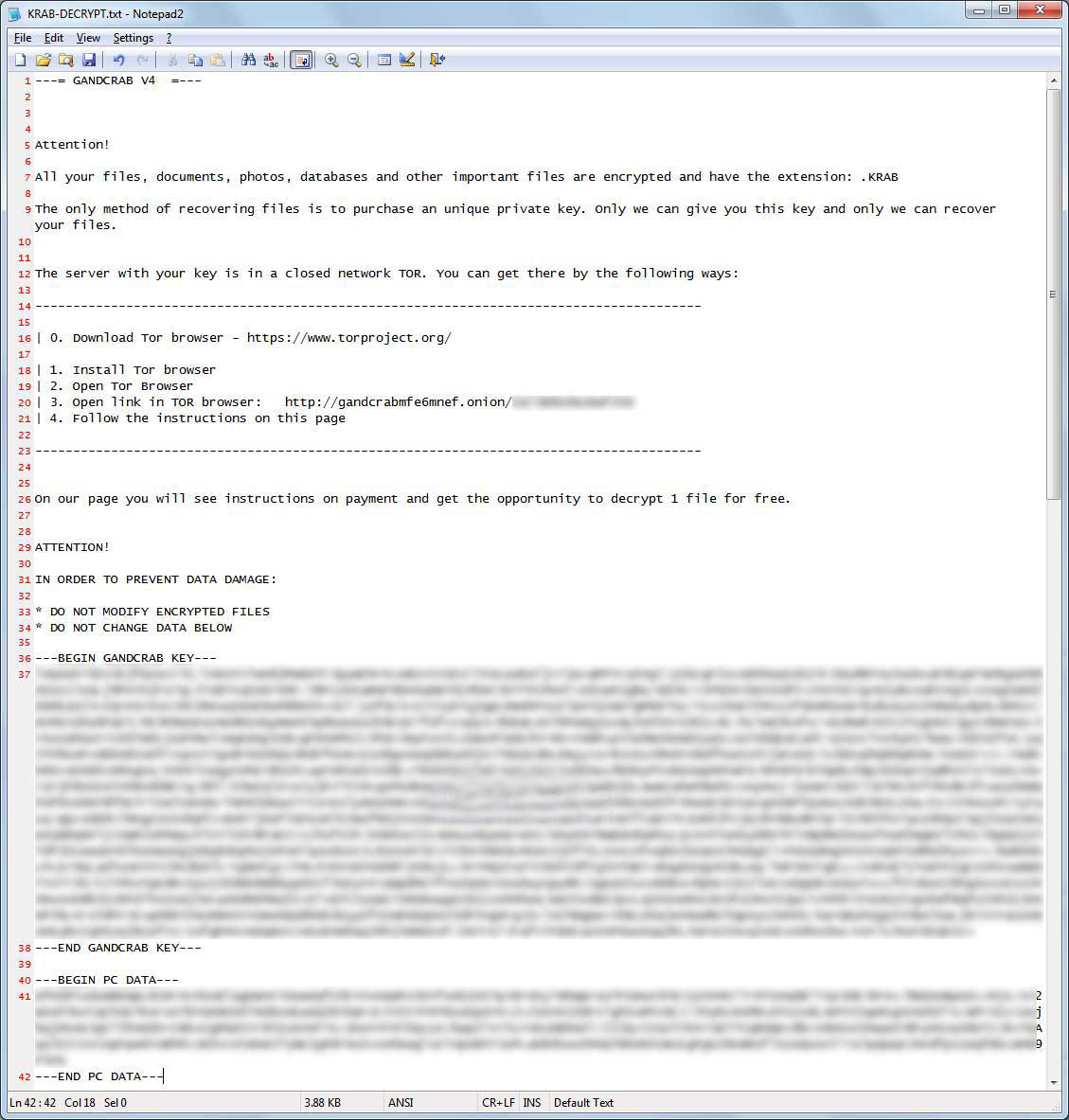
When encrypting files, the ransomware will also create ransom notes named KRAB-DECRYPT.txt that contains information about what happened to the victim’s files, a TOR site (gandcrabmfe6mnef.onion) to connect to for payment instructions, and encrypted information that the ransomware developers need to recover your encryption key.
You can see an example ransom note below.
If a user visits the TOR payment site they will be presented with the ransom amount and instructions on how to pay it in order to receive the GandCrab Decryptor.
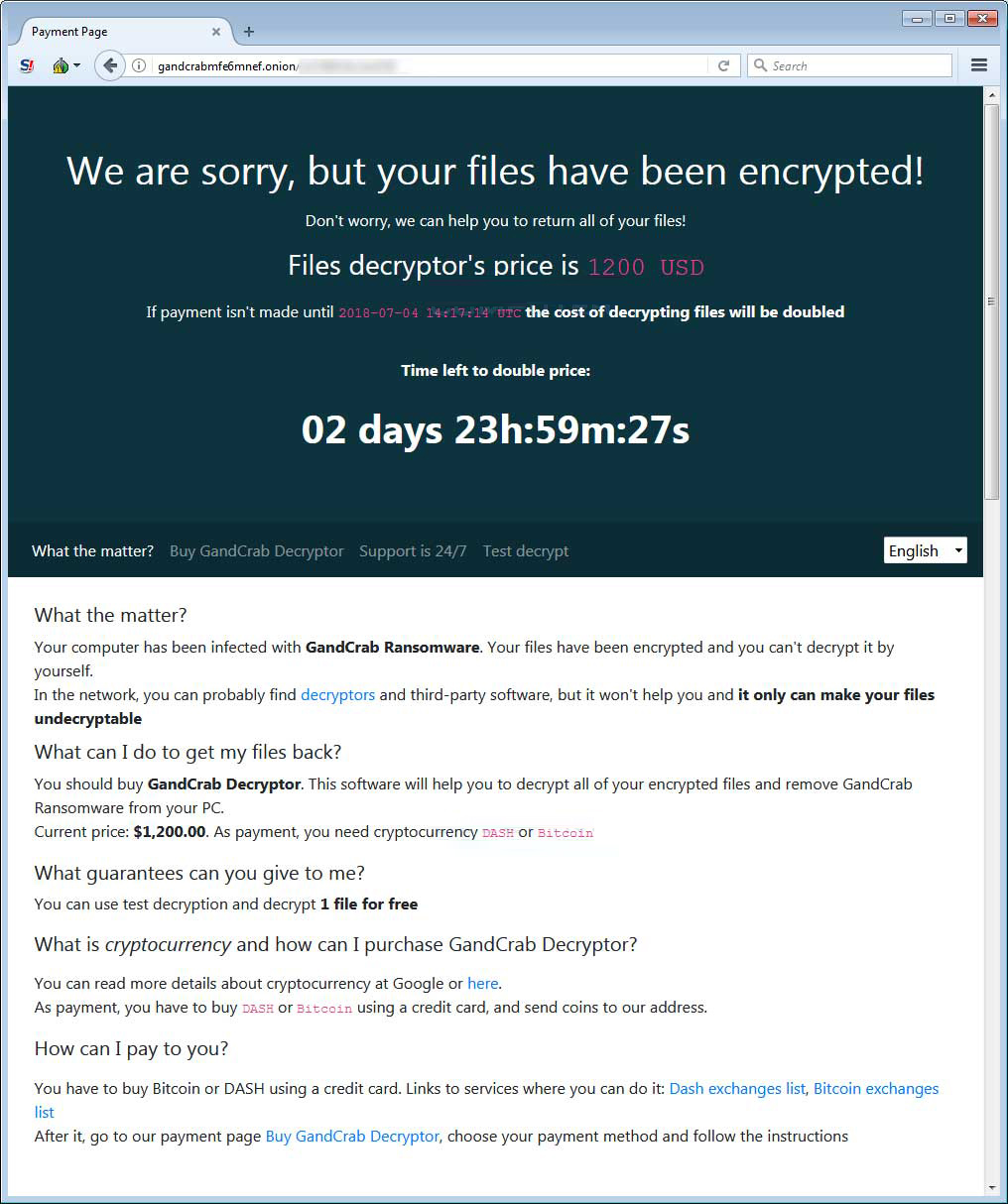
The ransom amount is currently $1,200 USD to be paid in the DASH (DSH) cryptocurrency as can be seen below.
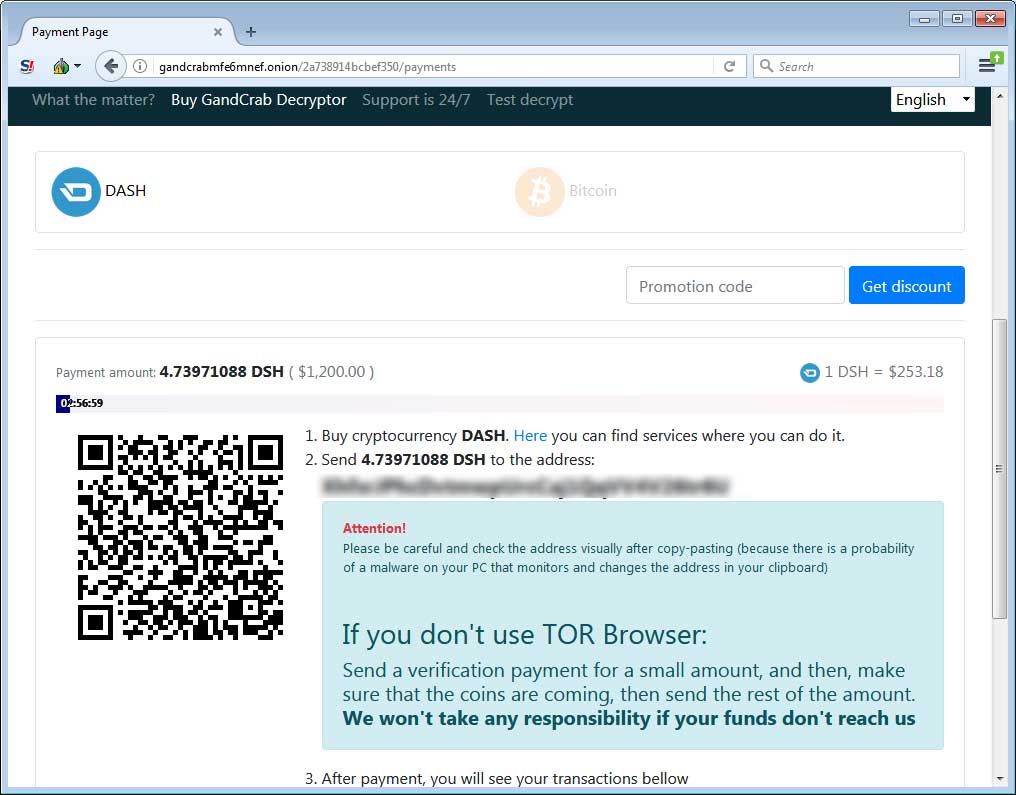
The TOR payment site also includes a support section where you can send messages to the developers and the ability to decrypt one file for free, so that they can prove they can do so.
It goes without saying that victims should make every effort not to pay the ransom. If you have a backup, even if its missing a few files, it is suggested that you still not pay the ransom.
As previously stated, at this time, victims of GandCrab v4 cannot decrypt their files for free. As always if you wish to discuss this ransomware or receive help with it.
How to protect yourself from the GandCrab Ransomware??
In order to protect yourself from ransomware it is important that you use good computing habits and security software. The most important step is to always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also make sure that you do not have any computers running remote desktop services connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
All Users are requested to:
- Install and keep NPAV updated up-to-date.
- Make sure NPAV Data Backup is ON.
- Always use trusted and secure sites for downloading setups.
