In a chilling revelation, researchers at Checkmarx have unearthed a nefarious scheme where threat actors are cunningly manipulating GitHub’s search algorithms to unleash persistent malware upon unsuspecting developers.
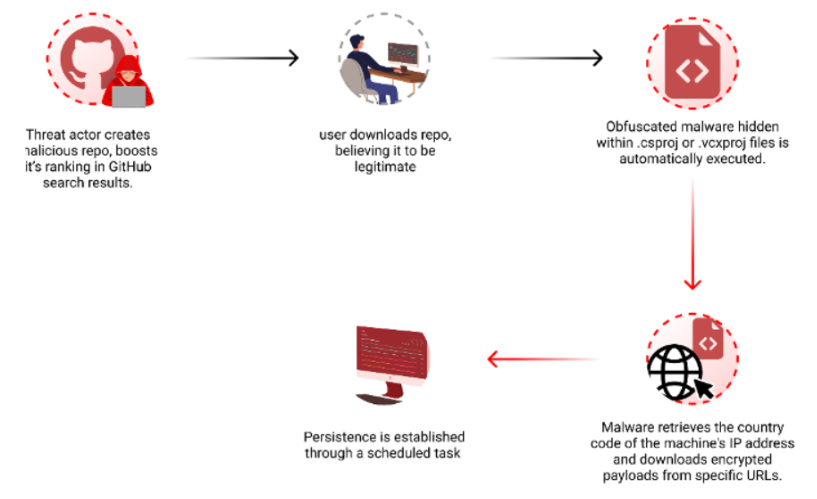
According to the report by Checkmarx, these malicious actors are employing sophisticated tactics to infiltrate developers’ systems. They craft malicious repositories disguised with innocuous names and topics, leveraging popular keywords to deceive users. Through techniques like automated updates and fake endorsements, they artificially inflate the repositories’ visibility in search results, making them more enticing to unwitting developers.
Utilizing GitHub Actions, the attackers orchestrate a relentless barrage of updates to their repositories, creating a façade of continuous activity. By strategically modifying files with timestamps or inconspicuous alterations, they dupe GitHub’s search algorithms into elevating their repositories’ rankings. Furthermore, employing multiple fake accounts to shower repositories with spurious stars adds a veneer of credibility, amplifying their allure to unsuspecting victims.
To evade detection, the threat actors cleverly conceal the malicious code within Visual Studio project files, ensuring automatic execution upon project build. This covert delivery mechanism allows the malware to fly under the radar, bypassing traditional security measures.
In a disturbing turn, the recent campaign has unveiled a sizable executable file reminiscent of the notorious “Keyzetsu clipper” malware. Targeting cryptocurrency wallets, this malicious payload poses a grave threat to users’ digital assets.
Maintaining persistence is paramount for these malevolent actors. They achieve this by creating scheduled tasks that clandestinely execute the malware daily, evading user scrutiny and perpetuating their malicious agenda.
The implications of these findings are dire, highlighting the urgent need for heightened vigilance within the open-source community. Manual code reviews and the adoption of specialized malware detection tools are imperative to combat this growing menace. Mere reliance on vulnerability scans is no longer sufficient in the face of such sophisticated attacks.
The exploitation of GitHub’s search functionality by malicious actors underscores the vulnerabilities inherent in the open-source ecosystem. As developers, it’s incumbent upon us to remain vigilant and adopt robust security practices to safeguard against these insidious threats. By staying informed and employing proactive measures, we can fortify our defences and preserve the integrity of our codebase.
Let this serve as a clarion call to action – for only through collective awareness and concerted efforts can we stem the tide of cyber threats and secure the future of software development.
