Security researchers have discovered a straightforward method to introduce malware to a Microsoft Teams-using organization, despite the application’s limitations on files from outside sources.
Microsoft Teams, a communication and collaboration tool that is a part of the Microsoft 365 cloud-based services, has been embraced by businesses and has 280 million active users each month.
Attack Information
The attack works with Microsoft Teams that are configured by default, which allows communication with Microsoft Teams accounts that are located outside of the organization, sometimes known as “external tenants.”
Even while this communication link would be adequate for phishing and social engineering assaults, the approach they discovered is more potent because it enables sending a malicious payload directly to a target’s inbox. Client-side security measures are in place in Microsoft Teams to prevent file delivery from external tenant accounts.
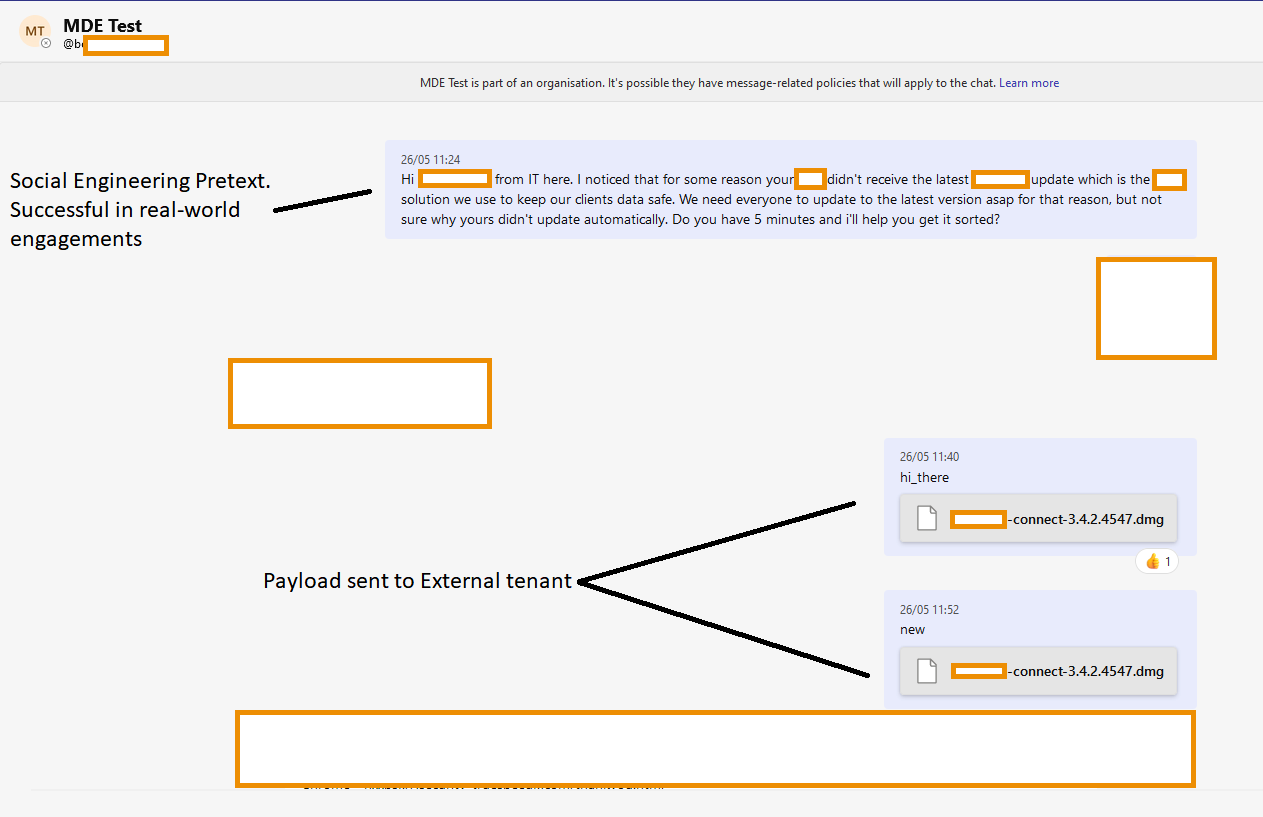
Attack illustration where the sender pretends to be a member of the IT staff (Jumpsec)
By altering the internal and external recipient IDs in the POST request of a message, an attacker can get past the restriction and trick the system into treating an external user as an internal one.
When the payload is sent in this manner, it is actually housed on a Sharepoint domain, where the recipient downloads it. However, it displays as a file, not a link, in the target inbox. The method was tried out in the real world, and as part of a covert red team engagement, the researchers were able to effectively deliver a command and control payload into an organization’s mailbox.
Install NPAV on your systems to ensure best-in-class security against malware and ransomware attacks. Use NPAV and join us on a mission to secure the cyber world.
