Email phishing continues to evolve as cybercriminals become more sophisticated in their tactics. One prevalent form of email phishing involves attackers masquerading as legitimate individuals or trusted contacts to deceive unsuspecting victims. In this blog, we will delve into the world of phishing attacks where attackers claim to be genuine persons and explore how you can protect yourself from falling victim to these deceptive ploys.
The Impersonation Game: In this type of phishing attack, cybercriminals go to great lengths to impersonate real individuals whom you may know or trust. They may pose as colleagues, friends, family members, or even professionals like your bank representative or a government official. By assuming a familiar identity, attackers aim to exploit your trust and manipulate you into divulging sensitive information or performing certain actions.
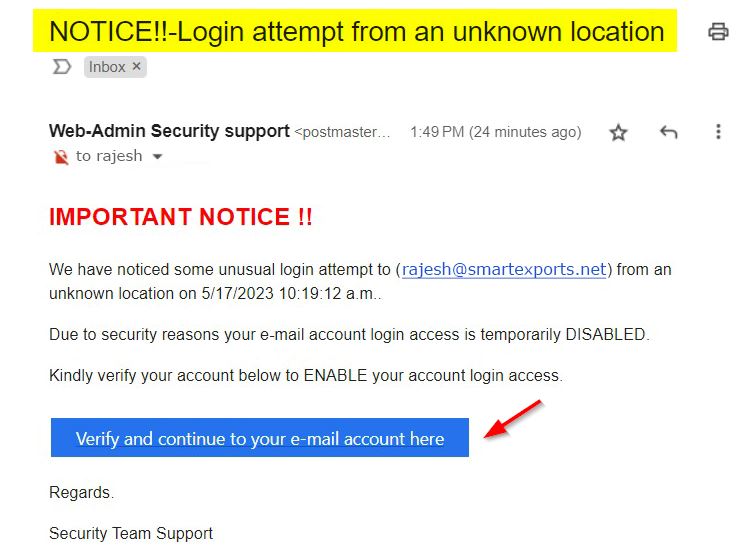
Here attacker claims that an attempt has been made to log in from an unknown location and an attacker is trying to help you to protect your login credentials.
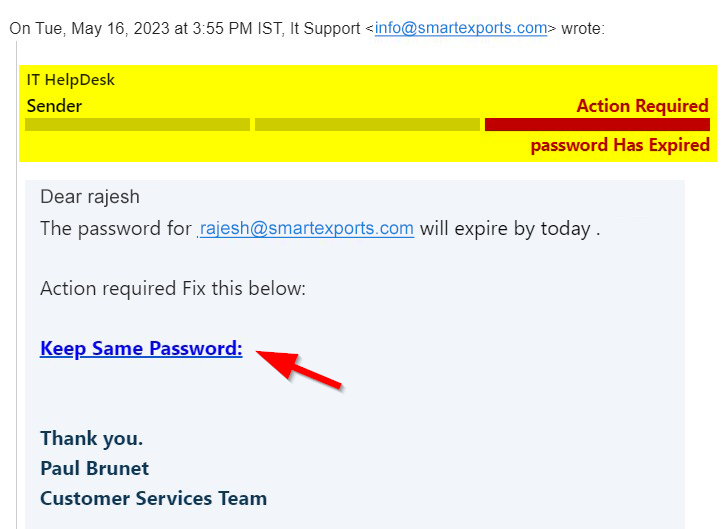
Here attacker claims to be a legitimate individual trying to help you in changing password
Red Flags to Detect Impersonation Email Phishing: While attackers may be skilled at mimicking legitimate individuals, there are warning signs you can watch out for to avoid falling into their traps:
a. Email address mismatch: Scrutinize the sender’s email address closely. Attackers often use similar but slightly altered email addresses to fool recipients. Check for misspellings, extra characters, or unfamiliar domain names.
b. Unusual tone or language: If you receive an email with an unexpectedly different tone or style compared to the person you know, exercise caution. Phishers may lack knowledge of the person they are impersonating, resulting in noticeable discrepancies.
c. Urgent or suspicious requests: Be wary of emails that convey a sense of urgency, demand immediate action, or request sensitive information, such as passwords, social security numbers, or financial details. Legitimate individuals often communicate important matters through secure channels.
Install NPAV on your systems to ensure best-in-class security against malware and ransomware attacks. Use NPAV and join us on a mission to secure the cyber world.
