Hackers are infecting devices with spyware malware that harvests call logs, texts, and GPS positions from phones by utilizing the phony Android app ‘SafeChat’. The Android spyware is thought to be a variation of “Coverlm,” which steals data from messaging apps like Facebook Messenger, Telegram, Signal, WhatsApp, and Viber.
The campaign is being run by the Indian APT hacking outfit “Bahamut,” whose most recent attacks have been primarily spear phishing messages on WhatsApp that transfer the harmful payloads directly to the victim.
Additionally, the analysts point out a number of TTP parallels to the ‘DoNot APT’ (APT-C-35), another state-sponsored threat group from India that has already infected Google Play with spyware-emulating chat apps. ESET revealed before the end of last year that the Bahamut group was employing phony Android VPN apps with substantial spyware features.
“Safe Chat” information
It’s common for victims to be convinced to download a chat app under the pretence of moving the conversation to a safer platform.
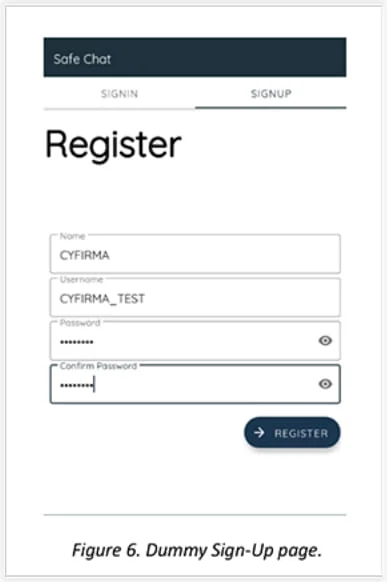
According to the analysts, Safe Chat has a deceptive user interface that makes it seem like genuine chat software. It also leads the victim through what appears to be a valid user registration process, which lends credibility and works as a great cover for spyware.
The acquisition of permissions to utilize the Accessibility Services, which are then abused to give the spyware greater permissions, is a crucial phase in the infection process. The spyware may access the victim’s contact list, SMS, call records, and external device storage, and retrieve accurate GPS position information from the infected device thanks to these extra rights.
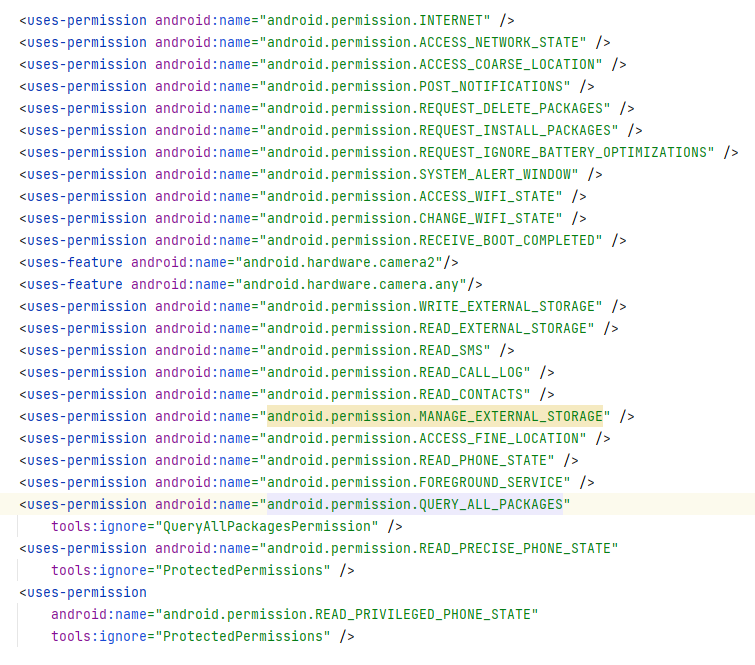
Permissions included in the spyware’s Manifest file
Exclusion from Android’s battery efficiency subsystem, which shuts down background processes when the user isn’t actively using the app, is another request made by the program to the user. The threat actor created the program to communicate with other chat applications that are already installed, according to another excerpt from the Android Manifest file.
OPEN_DOCUMENT_TREE permission will choose particular directories and access the apps stated in the intent. The interaction will be done via intents. Through port 2053, a specialized data exfiltration module sends information from the target device to the attacker’s C2 server.
Another module that is capable of RSA, ECB, and OAEPPadding is used to encrypt the stolen data. In addition, the attackers employ a “letsencrypt” certificate to thwart any network data eavesdropping attempts.
