The Enlisted multiplayer first-person shooter is the target of a ransomware operation that spreads trojanized versions of the game to Russian gamers through a bogus website.
Given that the game is free, threat actors may easily download the publisher’s installer, change it, and use it to disseminate malicious payloads to unwary consumers.
Between 500,000 and one million gamers actively participate in Enlisted, a legitimate game released by Gaijin Entertainment in 2021.
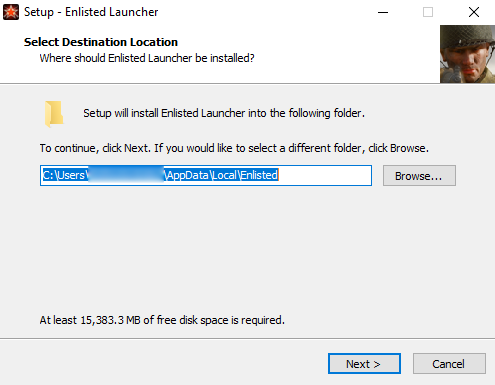
Using the malicious installer (Cyble)
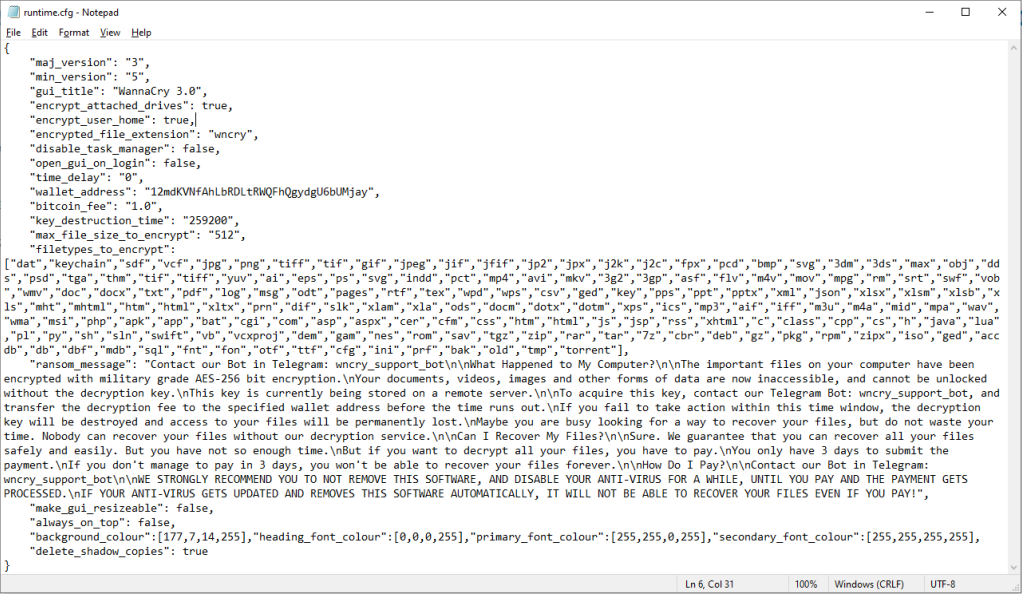
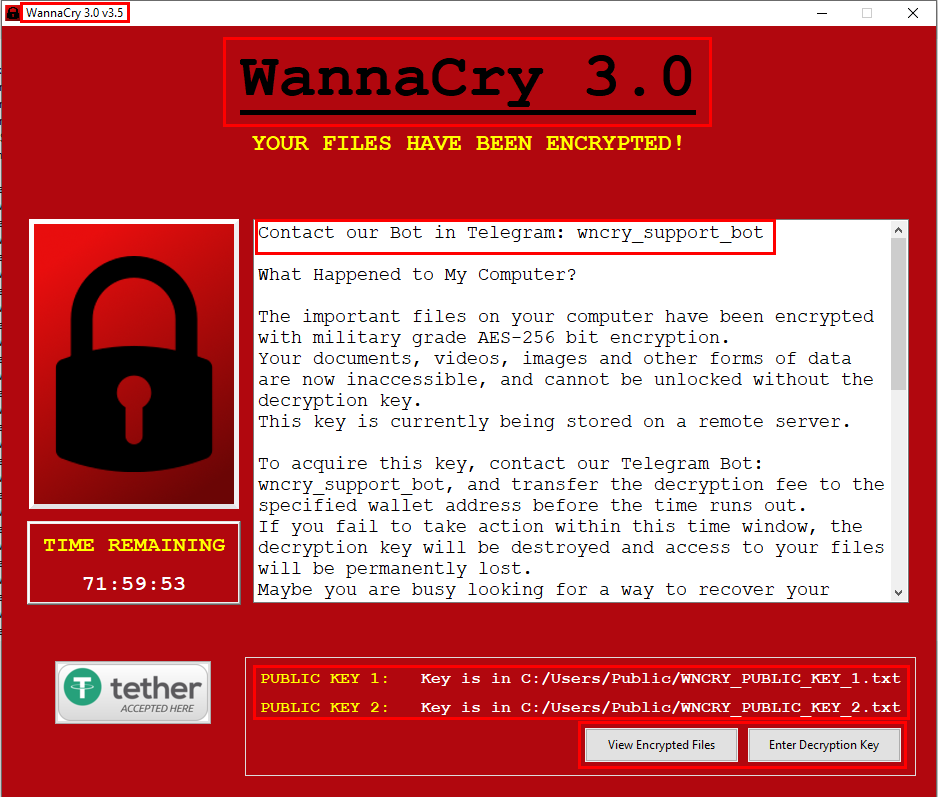
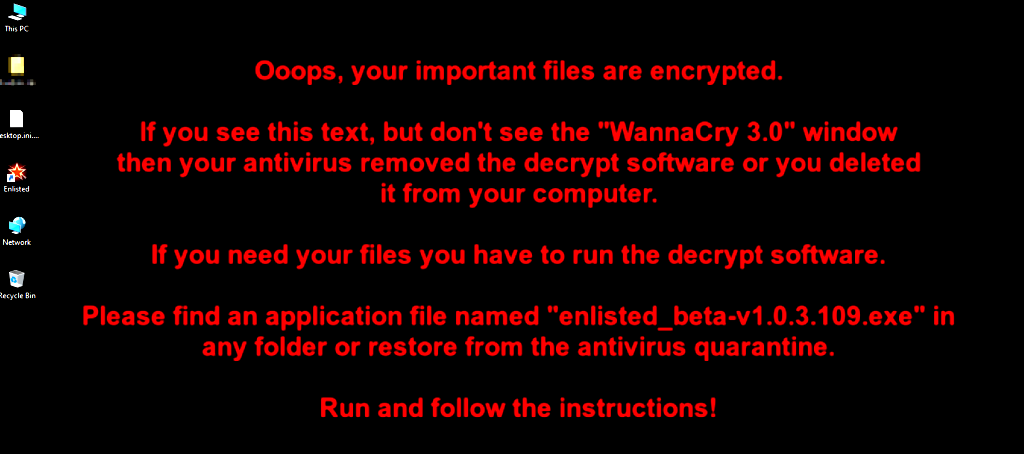
The malware that comes with the installation of the game poses as the third major iteration of the infamous WannaCry ransomware, even using the .wncry file extension on encrypted data.
recruited by ransomware The new “WannaCry” variety is said to be built on the open-source “Crypter” Python locker, which was obviously created for instructional purposes, according to Cyble’s researchers who examined the strain.
It should be noted that this is not the first time someone has tried to mimic WannaCry; most likely, this was done to terrify victims and get a rapid ransom payment.