In the ever-expanding digital landscape, where convenience and connectivity reign supreme, the security of personal data often hangs precariously in the balance. Recent revelations by a trio of cybersecurity researchers have shed light on a startling reality: close to 19 million plaintext passwords, along with a plethora of sensitive user information, have been left exposed on the public internet due to misconfigured instances of Firebase, a platform developed by Google for hosting databases, cloud computing, and app development.
The researchers, known as Logykk, xyzeva/Eva, and MrBruh, embarked on a meticulous journey through the digital realm, scanning over five million domains. Their findings were alarming: 916 websites, belonging to various organizations, either lacked proper security measures or had them set up incorrectly. Within these vulnerable instances, they unearthed more than 125 million sensitive user records, comprising emails, names, passwords, phone numbers, and even billing information with bank details.
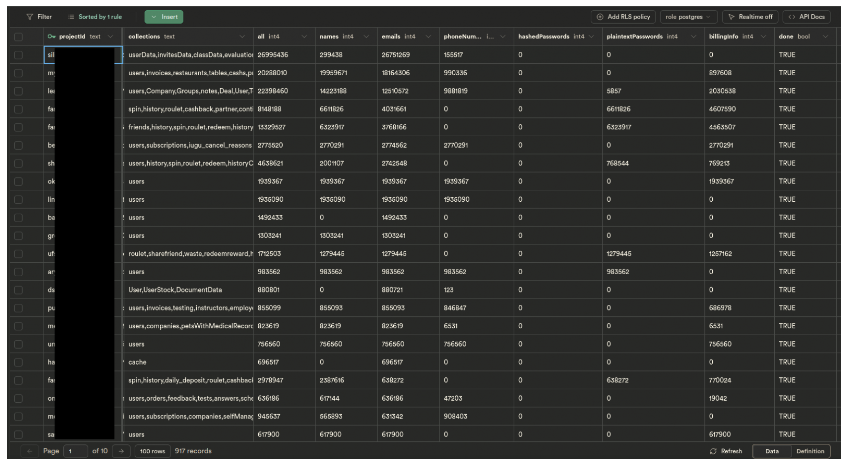
Database with samples of exposed user records, as per xyzeva.
One of the most troubling discoveries was the sheer volume of plaintext passwords—nearly 98% of them were exposed in their raw form, totalling close to 20 million. This revelation raises serious concerns, especially considering Firebase offers robust solutions, like Firebase Authentication, designed to safeguard user credentials.
The process of alerting affected companies was not without its challenges. Despite sending out 842 emails over a span of 13 days, only a fraction of site owners responded, albeit positively. However, some encounters with site administrators proved less than fruitful, with instances of mockery and unprofessionalism tarnishing the discourse.
Notably, one Indonesian gambling network emerged as a focal point, harbouring a staggering number of exposed bank account records and plaintext passwords. This incident underscores the global reach and ramifications of lax cybersecurity practices.
The researchers’ journey was marked by perseverance and innovation. Their initial Python script, while promising, faced limitations due to memory consumption. This setback prompted the development of a more efficient variant in Golang, which ultimately facilitated the comprehensive scanning of over five million domains.
Despite their significant findings, the researchers emphasize that the disclosed figures likely represent only a fraction of the actual scope of the issue. The true extent of exposed records may be far greater—a sobering realization in an age where data privacy is paramount.
The genesis of this investigation traces back to a prior project, where the researchers uncovered vulnerabilities within Firebase instances utilized by Chattr, an AI-powered hiring software solution. The implications were profound, potentially granting unauthorized access to sensitive hiring data of major fast-food chains across the United States.
While responsible disclosure led to the resolution of the Chattr incident, it serves as a poignant reminder of the ever-present risks posed by misconfigured Firebase instances and the critical importance of proactive cybersecurity measures.
As we navigate an increasingly interconnected digital landscape, the onus falls upon organizations to prioritize robust security practices, lest they fall victim to the perils of data exposure and exploitation.
