Bitter Cyberspies Target Defense Organizations with Advanced MiyaRAT Malware

The 'Bitter' cyberespionage group has launched attacks on Turkish defense organizations, deploying a new malware family, MiyaRAT. This sophisticated malware, alongside WmRAT, leverages alternate data streams and advanced techniques to exfiltrate sensitive data and control compromised systems.
Bitter Group: A South Asian cyberespionage entity active since 2013, known for targeting government and critical organizations in Asia.
New Malware – MiyaRAT: Advanced malware with refined features like encryption, reverse shell capabilities, and enhanced file control, used selectively for high-value targets.
Attack:
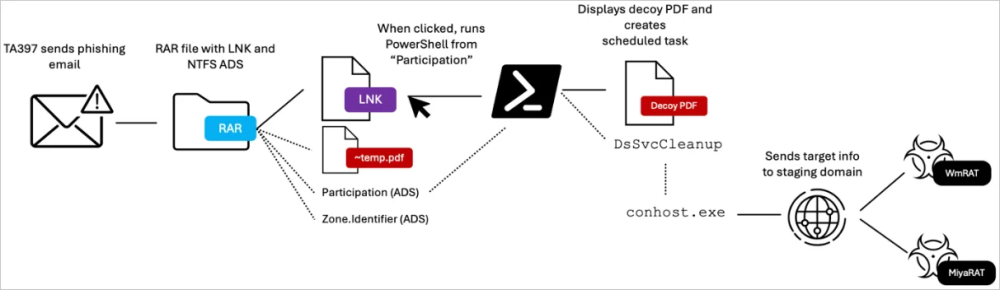
- Phishing emails with malicious RAR attachments containing decoy PDFs and disguised shortcut files (.lnk).
- PowerShell commands executed via alternate data streams (ADS), creating a scheduled task for continuous malicious activity.
- Use of staging domains to fetch payloads like WmRAT and MiyaRAT.
MiyaRAT vs. WmRAT: While both are capable of data theft and system control, MiyaRAT features superior encryption and control mechanisms, making it a preferred tool for critical operations.
IoCs & Detection: Proofpoint has shared Indicators of Compromise (IoCs) and a YARA rule for threat detection in their detailed report.
The emergence of MiyaRAT highlights the evolving sophistication of cyberespionage campaigns targeting critical sectors. Net Protector Cyber Security advises organizations to enhance their defenses by monitoring IoCs, implementing strict email security protocols, and staying updated on emerging threats. Advanced endpoint protection and regular vulnerability assessments can help mitigate risks posed by such targeted attacks.






