Data Breach
-
Read moreChina-linked Lotus Blossom group breached Notepad++ hosting, delivering Chrysalis backdoor via tampered updates. Learn the attack details and how to stay safe.
-
Posted: January 20, 2026Views: 266Read moreUrgent alert: McDonald's India reportedly targeted by the Everest ransomware group. Over 861 GB of data compromised. Learn the details and how to secure your account
-
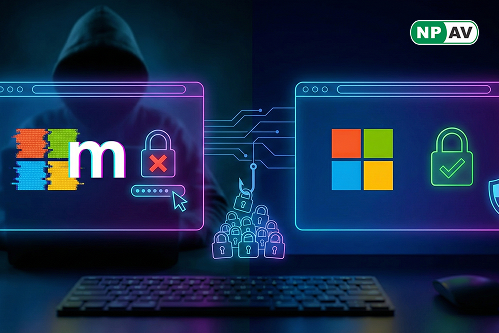
Read moreDiscover how hackers use 'rn' instead of 'm' in fake Microsoft domains to steal logins via phishing. Learn common typosquatting tricks and how to stay safe online.
-
Read morePhishing scams with fake invoices deploy XWorm—learn the tactics, risks, and defenses to avoid credential theft and ransomware.
-
Read moreMedusa and DragonForce use SimpleHelp flaws for attacks—learn about the tactics, impacts, and defenses against supply chain ransomware.
-
Read moreZoom vulnerabilities allow unauthorized access—learn about the CVEs, risks, and urgent update needs to secure your video calls.
-
Read moreConstruction targeted by APT groups—learn about credential theft, social engineering, and defenses to protect your firm's data.
-
Read moreCVE-2025-23358 in NVIDIA App allows code execution—learn about the risk, affected versions, and urgent patching steps.
-
Read moreFIN7 uses SSH backdoor for remote access—learn about the tactics, persistence, and defenses to protect against this advanced threat.
-
Read moreHackers stole and sold 50,000 CCTV clips from Rajkot hospital—learn about the breach, methods, and tips to secure surveillance systems.