Hackers Clone Google Chrome Install Page to Spread Dangerous Android Malware

Cybersecurity experts have uncovered a dangerous malware campaign where hackers mimic the Google Chrome install page to trick Android users into downloading a powerful spying tool called SpyNote.
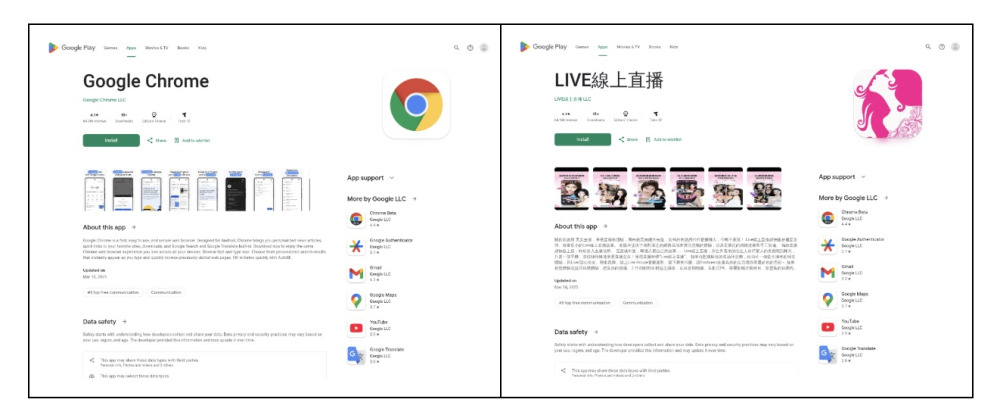
These fake pages look nearly identical to the real Google Play Store and are hosted on newly registered shady domains. When users fall for the trick and install the app, they unknowingly give hackers full control of their device.
Fake Chrome Install Pages
- Hackers built fake websites that look just like Google Chrome’s official page on the Play Store.
- These sites are used to trick users into downloading malware disguised as a Chrome browser app.
SpyNote RAT: A Serious Threat
The malware (SpyNote) allows attackers to:
- Read SMS messages and contact lists
- Track GPS location
- Record phone calls
- Use cameras and microphones remotely
- Capture login details with keylogging
- Bypass 2FA using Accessibility Services
Targets Include Businesses & Personal Users
- The malware is especially dangerous for companies that allow employees to use personal devices at work.
- Once infected, a phone may act as a gateway into corporate networks.
How the Malware Works
- A fake Chrome page triggers a malicious APK download using hidden JavaScript.
- It drops the SpyNote malware in two stages — the second stage enables full spying capabilities.
- The malware connects to remote servers using port 8282 and known malicious IP addresses.
Technical Clues Point to China
- The hackers use a mix of English and Chinese in their code and comments.
- They registered domains through NameSilo and XinNet, and used hosts like LightNode and Vultr.
This attack shows how far cybercriminals will go to steal your data — even by perfectly imitating trusted platforms like Google Play. Always download apps directly from verified stores, avoid clicking on links from unknown sources, and keep your security software updated.






