Hackers Exploit ClickFix Tactic to Gain Full Control Over Windows Machines

A new phishing campaign is targeting Windows users with a deceptive technique called ClickFix, tricking victims into executing malicious PowerShell commands. The attack, active since March 2025, deploys a modified version of the Havoc command-and-control (C2) framework through SharePoint abuse, allowing attackers to take full control of compromised systems.
- Hackers send phishing emails disguised as urgent document notifications. Victims are instructed to copy and paste a PowerShell command to fix a fake error message.
- The PowerShell script retrieves a malicious payload from a SharePoint link controlled by attackers, bypassing traditional security measures.
- The malware checks for sandbox environments, establishes persistence, and downloads a Python interpreter if necessary. It then loads a hidden malicious DLL without leaving traces on disk.
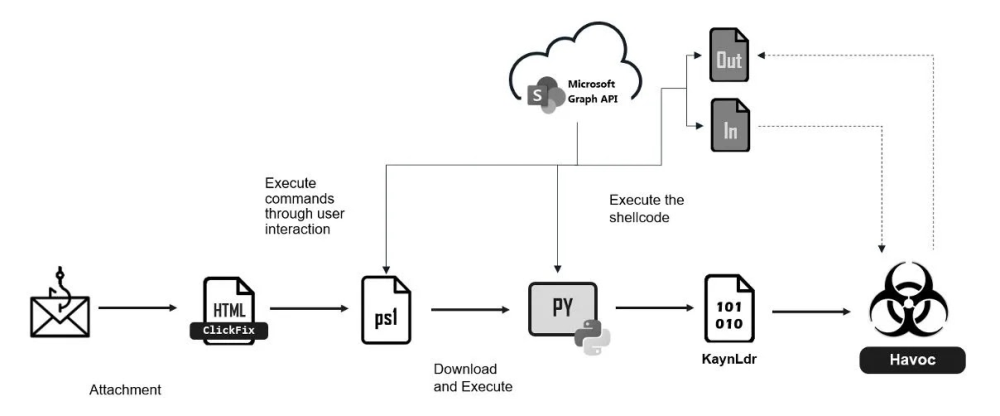
- The final payload is a modified Havoc post-exploitation tool, which masks its traffic using Microsoft Graph API to blend with legitimate cloud service activity.
- The malware uses AES-256 encryption and SharePoint API calls to send stolen data and receive attacker commands, erasing traces immediately after execution.
- Fortinet has issued security signatures to block the attack chain and advises organizations to train employees, monitor SharePoint activity, and restrict PowerShell execution to prevent exploitation
This attack highlights the growing sophistication of phishing campaigns that combine social engineering, open-source malware, and cloud abuse to evade detection. Organizations must stay vigilant, monitor cloud API usage, and implement strict PowerShell execution policies to defend against such threats.
Stay Secure with Net Protector Cyber Security!
Comment(s)






