Jupyter infostealer malware is stealing Chrome and Firefox data
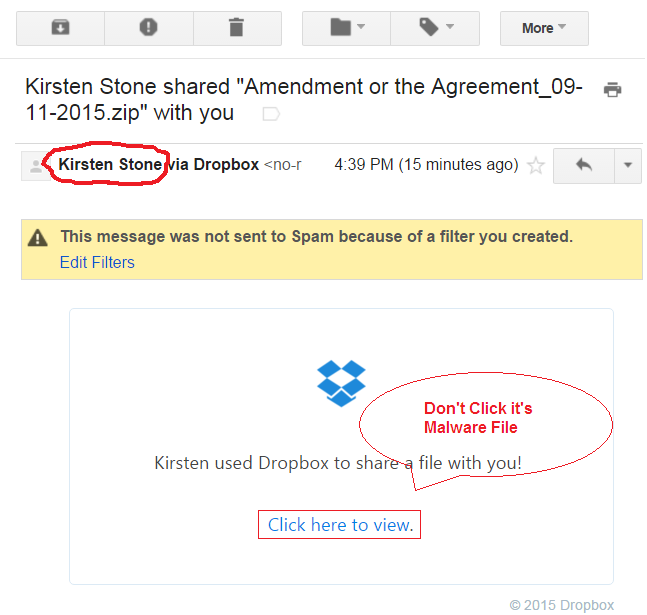
New information stealer malware dubbed as Jupyter is targeting web browser data.
Jupyter is an infostealer malware which is operated by Russian hackers. Infostealer malware is used by hackers to steal sensitive information from the targeted system. The malware connects to its server and uploads the stolen data, which can later be used by hackers.
Researchers have found that Jupyter is written in .NET and targets notable web browsers such as Mozilla Firefox and Google Chrome. The malware has the capability of downloading and running malware plus Powershell scripts and commands while also injecting shellcode.
The malware file appears to be an authentic installation file in ZIP format. The alarming situation is that the malware has a detection rate of 0% in six months, which means that there are plenty of devices under undetected attacks.
Researchers have conducted research operations on this malware and its C2 servers. The command servers are present in the Russian region and many of them are inactive as suggested by the latest reports.
NPAV recommends users to always use authentic and genuine websites for downloading files. Using an untrusted source for downloading can bombard your device with malware. Users must properly check the authenticity of every downloaded file as they may contain hidden malicious elements.
Install NPAV on your devices to keep them protected from all kinds of cyberattacks. Use NPAV and join us on a mission to secure the cyber world.






