Massive Data Breach: 81.5 Crore Citizens’ Covid-19 Test Data for Sale via ICMR
Suspected to be the most extensive data breach in the country’s history, sensitive information of 81.5 crore Indians linked with the Indian Council of Medical Research (ICMR) is reportedly up for sale.
In light of the severity of the situation, the Central Bureau of Investigation (CBI), India’s premier agency, is expected to launch an investigation into the matter once ICMR files a formal complaint.
A ‘threat actor’ going by the name of X, formerly active on Twitter, has advertised the compromised database on a dark web breached forum, which includes data pertaining to 815 million Indian citizens. This includes Aadhaar and passport information, as well as names, phone numbers, and addresses. The ‘threat actor’ asserted that the data, obtained from the Covid-19 testing records, originated from ICMR.

ICMR has reportedly faced multiple cyber-attack attempts since February, with central agencies and the council being aware of these incidents. Approximately 6,000 hacking attempts were made on ICMR servers last year. It is reported that the concerned agencies had advised ICMR to take corrective action to prevent any data breaches.
Efforts to reach the ICMR DG for comment on Saturday went unanswered, and a response is still awaited.
It has come to light that CERT-In has notified ICMR about the breach, and the sample data available for sale corresponds to the actual data of ICMR. This prompted the involvement of multiple agencies.
Given the seriousness of the situation, senior officials from various agencies and ministries have been brought in. As foreign actors are allegedly implicated in the breach, the involvement of a leading agency for the investigation is deemed crucial. Immediate remedial measures have been implemented, and the necessary standard operating procedure has been put in place to mitigate the impact.
Sources have confirmed that the source of the leak remains unidentified, as segments of the Covid-19 test data are distributed to the National Informatics Centre (NIC), ICMR, and the Ministry of Health.
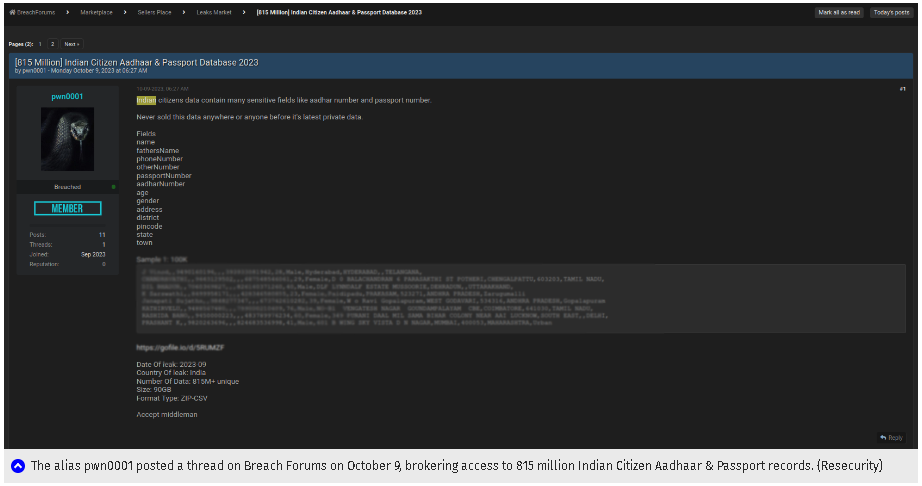
According to the American cybersecurity and intelligence agency Resecurity, which first detected the breach, a threat actor using the alias ‘pwn0001’ posted a thread on Breach Forums on October 9, offering access to 815 million records of “Indian Citizen Aadhaar & Passport.” This number is significant considering India’s population, which is just over 1.486 billion.
Pwn0001 shared spreadsheets containing four extensive data samples, which included fragments of Aadhaar data as proof. Resecurity stated, “One of the leaked samples contains 100,000 records of PII related to Indian residents. In this sample leak, HUNTER analysts identified valid Aadhaar Card IDs, which were corroborated via a government portal that provides a ‘Verify Aadhaar’ feature, allowing people to validate the authenticity of Aadhaar credentials.”






