Ransomware Gang Exploits SSH Tunnels to Attack VMware ESXi Servers

Hackers are using SSH tunnels to secretly access VMware ESXi servers, steal data, and deploy ransomware. These servers, which host multiple virtual machines, are critical to businesses but are often not well-monitored. Attackers take advantage of these gaps to lock down systems and demand ransom payments.
VMware ESXi Servers Are Prime Targets:
- VMware ESXi servers are valuable because they host multiple virtual machines on one system. If attackers gain control of the ESXi server, they can shut down all the virtual machines at once, causing major disruptions.
How Hackers Break In:
- Attackers exploit known software vulnerabilities or use stolen admin credentials to access the ESXi server.
Hackers Use SSH for Their Attacks:
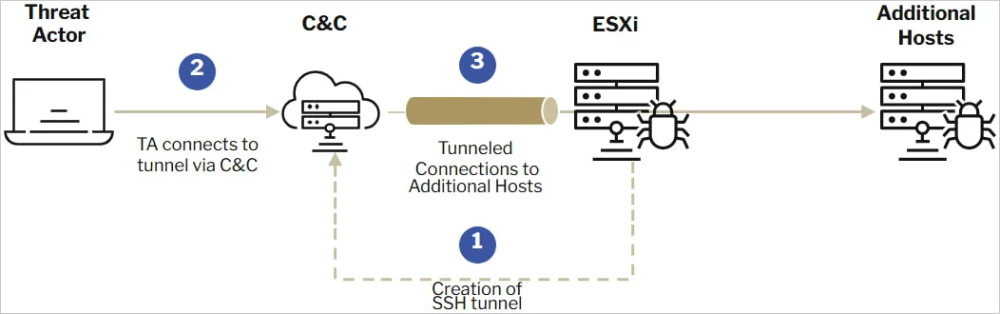
- VMware ESXi has a built-in SSH feature for remote management, which attackers misuse.
- SSH tunnels allow hackers to move within the network unnoticed and install ransomware without raising alarms.
- Using simple SSH commands, they can create hidden connections to their own servers and stay undetected.
Logs Make Investigation Harder:
- ESXi logs are scattered across multiple files, which makes tracking suspicious activity difficult.
- Hackers erase or alter logs to hide evidence of their activities, making it even harder for businesses to investigate.
Logs to Watch for Signs of Attacks:
System admins should keep an eye on these files to detect hacking attempts:
- /var/log/shell.log – Tracks commands run in the ESXi shell.
- /var/log/hostd.log – Logs admin activities and user logins.
- /var/log/auth.log – Captures login attempts and authentication details.
- /var/log/vobd.log – Records system and security events.
What Hackers Do Once Inside:
- Encrypt important virtual machine files, making them inaccessible.
- Demand ransom payments and threaten to delete or leak data if their demands aren’t met.
Steps to Protect Your ESXi Servers:
- Disable SSH: Turn off SSH on ESXi servers unless absolutely necessary. If needed, only enable it temporarily.
- Centralize Logs: Use tools to gather and monitor all log files in one place for better visibility.
- Keep Systems Updated: Regularly install patches and updates to fix security gaps.
- Restrict Access: Use strong passwords, multi-factor authentication, and limit admin privileges to reduce risks.
VMware ESXi servers are critical but often overlooked when it comes to security. Hackers are exploiting these gaps using SSH tunnels to launch ransomware attacks and cause widespread damage. To prevent such incidents, businesses need to strengthen their security measures, regularly update systems, and actively monitor server activity. Taking these steps can help protect against devastating ransomware threats.






