TeamTNT Launches New Cloud Attacks on Docker for Cryptomining and Profit

TeamTNT, a notorious hacking group specializing in cryptojacking, has unleashed a new wave of cyberattacks aimed at cloud-native environments. Exploiting exposed Docker APIs, the group is deploying malware and cryptominers, utilizing breached Docker instances for cryptocurrency mining and renting the compromised infrastructure for profit. This multi-stage campaign highlights the need for vigilant cloud security to prevent unauthorized access and cryptomining activity.
- Cloud Attack Evolution: TeamTNT's latest campaign focuses on cloud-native environments, specifically Docker, to hijack resources for cryptomining.
- Docker Daemon Exploits: They target unauthenticated Docker APIs using specialized scripts and scanning tools, such as masscan and ZGrab, to locate vulnerable endpoints.
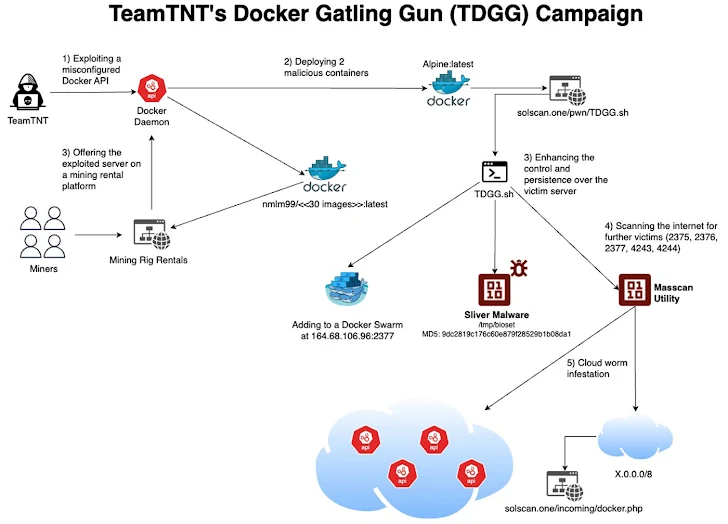
- Malware Deployment: The group leverages Docker Hub to distribute malware, deploying the Sliver command-and-control (C2) framework for remote control of infected servers.
- Dual Purpose Infrastructure: The compromised Docker environments are used for mining Monero (XMR) and are also rented to third parties on Mining Rig Rentals for additional revenue.
- Persistence & Anonymity: TeamTNT maintains C2 through services like AnonDNS to mask their command servers and utilizes Docker Swarm to strengthen the campaign's resilience.
- Prometei Botnet Spread: In addition to TeamTNT's operations, a separate Prometei botnet targets vulnerable RDP and SMB protocols, furthering cryptojacking efforts.
The return of TeamTNT with enhanced cloud attack tactics showcases the persistent risk of cryptojacking within cloud infrastructure. Fortifying security measures with Net Protector Cyber Security products, such as Cloud Protection and Endpoint Security, provides businesses with robust monitoring, threat detection, and vulnerability management to prevent unauthorized Docker access and cryptomining exploits.






