Beware of Fake Resumes: More_eggs Malware Targets Recruiters in Phishing Attack

In the ever-evolving landscape of cybersecurity threats, a new phishing campaign has emerged, targeting recruiters with the More_eggs malware disguised as resumes. First detected over two years ago, this technique has resurfaced, posing a significant threat to unsuspecting victims.
In May 2024, cybersecurity firm eSentire identified an unsuccessful phishing attempt targeting a recruiter at an unnamed industrial services company. The attackers, posing as job applicants, lured the recruiter to a malicious website to download a resume, which in reality, was a loader for the More_eggs malware.
What is More_eggs?
More_eggs is a modular backdoor malware developed by a threat actor known as Golden Chickens, also referred to as Venom Spider. This malware is offered under a Malware-as-a-Service (MaaS) model, allowing other cybercriminals to use it to harvest sensitive information. In 2023, eSentire exposed two individuals, known as Chuck from Montreal and Jack, who are believed to be behind the operation.
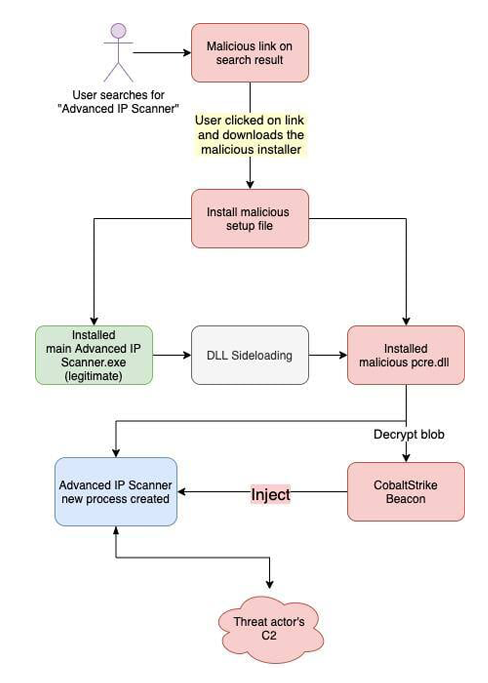
credit: The hacker news
The latest campaign involves responding to LinkedIn job postings with a link to a fake resume download site. This leads to the download of a malicious Windows Shortcut file (LNK). When the LNK file is executed, it retrieves a malicious DLL using a legitimate Microsoft program (ie4uinit.exe) and executes it with regsvr32.exe. This process establishes persistence, gathers data about the infected host, and deploys additional payloads, including the More_eggs backdoor.
eSentire's analysis reveals that the More_eggs campaigns remain active. Cybercriminals continue to employ social engineering tactics, posing as job applicants to deceive recruiters into downloading their malware. Despite efforts to shut down these operations, the threat persists, highlighting the need for constant vigilance.
Broader Implications
This phishing attack is part of a larger trend of sophisticated social engineering campaigns. For example, eSentire also reported on a drive-by download campaign distributing the Vidar Stealer malware through fake websites for the KMSPico Windows activator tool. These sites are designed to evade detection by requiring human input to download malicious payloads.
Additionally, new phishing kits like V3B have emerged, targeting banking customers in the European Union. Offered as Phishing-as-a-Service (PhaaS) on the dark web, these kits come with localized templates to mimic banking authentication processes and advanced capabilities to steal credentials and one-time passwords.
To safeguard against these threats, individuals and organizations must:
Be Skeptical: Always verify the authenticity of emails and attachments, especially those from unknown senders.
Stay Updated: Keep software and systems up-to-date with the latest security patches.
Educate Employees: Conduct regular training sessions to help employees recognize phishing attempts and other cyber threats.
Use Security Tools: Implement robust security tools and practices, including firewalls, antivirus software, and intrusion detection systems.
In the fight against cybercrime, awareness and proactive measures are crucial. By staying informed and vigilant, you can protect yourself and your organization from falling victim to these sophisticated phishing attacks.






