Bootkitty: The First UEFI Bootkit Targeting Linux Unveiled by Researchers

Researchers have discovered "Bootkitty," the first-ever UEFI bootkit targeting Linux systems. Although currently a proof-of-concept, this development signals a critical shift in the UEFI threat landscape, historically dominated by Windows-focused attacks. Bootkitty demonstrates advanced capabilities, including bypassing Secure Boot protocols and disabling kernel integrity checks, emphasizing the need for robust cybersecurity measures to protect Linux environments.
First UEFI Bootkit for Linux: Bootkitty represents a significant milestone as the first-known UEFI bootkit targeting Linux systems, expanding the scope of UEFI threats beyond Windows platforms.
Proof-of-Concept: Currently not observed in real-world attacks, Bootkitty highlights potential vulnerabilities in Linux environments.
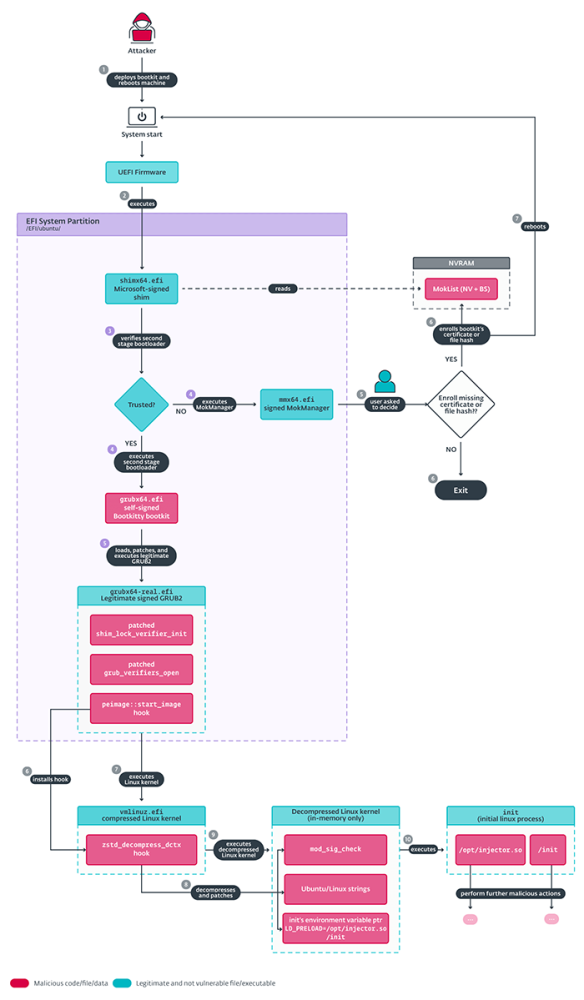
Key Capabilities: Disables kernel signature verification.
- Bypasses UEFI Secure Boot integrity checks through malicious hooks.
- Modifies the Linux init process to preload malicious ELF binaries.
- GRUB Bootloader Exploitation: Patches legitimate GRUB bootloader functions to bypass additional integrity checks.
Kernel Manipulation: Hooks UEFI authentication protocols to bypass secure boot mechanisms.
- Interferes with kernel decompression processes to load malicious modules.
- Utilizes the LD_PRELOAD environment variable to load malicious shared objects.
- Rootkit Features: Linked kernel modules provide rootkit capabilities, including file and process hiding and port opening.
No Active Deployment Yet: There is no evidence linking Bootkitty to real-world attacks or association with the ALPHV/BlackCat ransomware group.
Implications for Cybersecurity: This discovery highlights the evolving sophistication of Linux-targeted threats, necessitating enhanced vigilance and protection strategies.
Bootkitty signifies a turning point in the cybersecurity landscape by extending UEFI bootkit threats to Linux systems. Even as a proof-of-concept, its advanced capabilities reveal critical vulnerabilities that adversaries could exploit in the future. Organizations must strengthen defenses, ensure Secure Boot configurations, and proactively monitor for potential threats targeting Linux environments to stay ahead in an increasingly complex threat landscape. Net Protector Cyber Security remains committed to equipping clients with robust solutions to counter evolving cyber threats.






