Business Email Compromise: Detecting the Invisible Threat Before It Strikes

Business Email Compromise (BEC) attacks are stealthy, effective, and devastating. With no malware involved, these attacks bypass traditional security filters, trick employees, and siphon sensitive data or funds. But with real-time visibility through interactive sandboxing and endpoint protection like Net Protector, businesses can stay one step ahead.
- No malware required — BEC attacks rely purely on social engineering and user manipulation.
- Hosted on trusted platforms like OneDrive or Google Forms, making detection harder.
- Use redirect chains and CAPTCHA challenges to evade scanners.
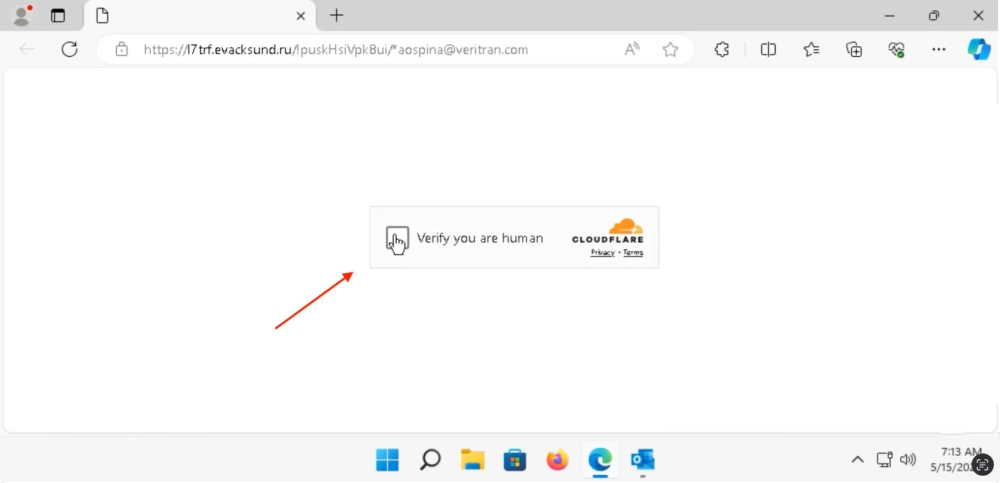
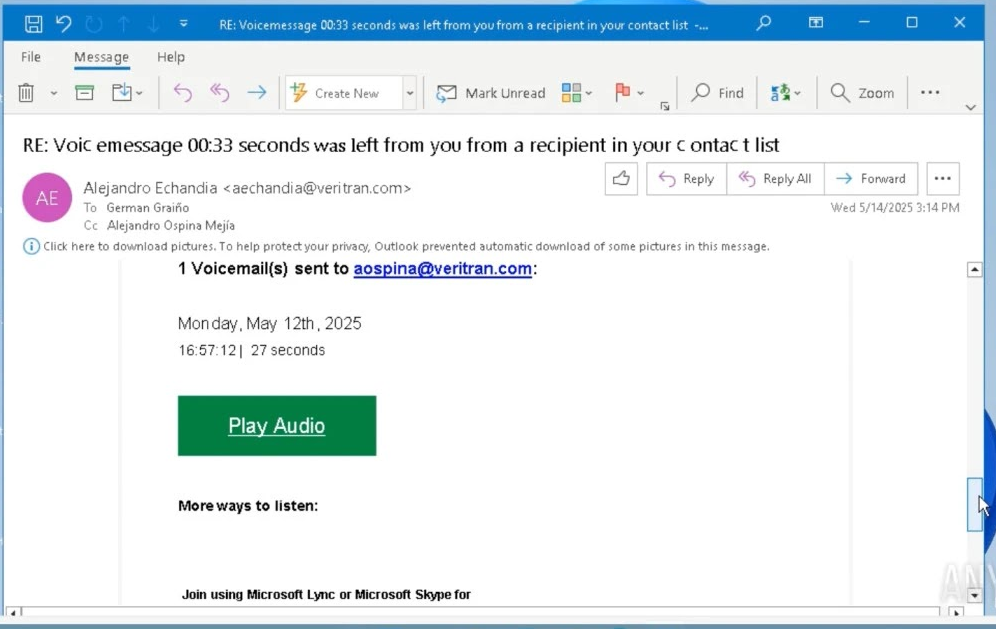
- Phishing emails mimic routine communications, often appearing as invoices or official requests.
- Interactive sandboxing (like ANY.RUN) reveals hidden attack flows within seconds.
- Features like Automated Interactivity simulate human behavior to trace phishing paths.
- Final payload often includes realistic fake login pages to steal credentials.
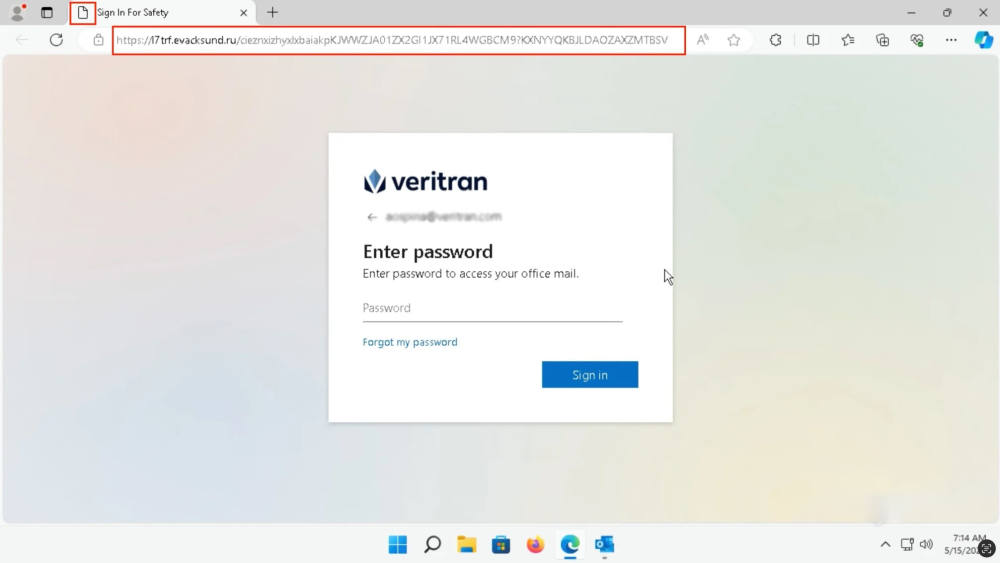
- Technical insights: Full process trees, real-time network traffic, Suricata alerts, and campaign tagging.
- IOCs (Indicators of Compromise) can be instantly exported for blocking and reporting.
- Assists both junior and senior analysts with a user-friendly interface and actionable intelligence.
BEC attacks may be invisible to conventional tools, but they’re not unstoppable. Platforms like ANY.RUN expose the full anatomy of these threats in real-time, empowering cybersecurity teams with unmatched visibility. And with Net Protector Endpoint Security, businesses of all sizes can stay protected against phishing, credential theft, and sophisticated social engineering attacks. Because in today’s threat landscape, visibility and speed are your best defense






