China-Linked Cyber Espionage Group Targets 70+ Organizations

A China-linked cyber espionage group has targeted over 70 organizations across various sectors, including government, media, manufacturing, finance, telecommunications, and research, between July 2024 and March 2025.
The reconnaissance activity, which included targeting American cybersecurity company SentinelOne, is attributed to a threat cluster called PurpleHaze, overlapping with known Chinese cyber espionage groups APT15 and UNC5174.
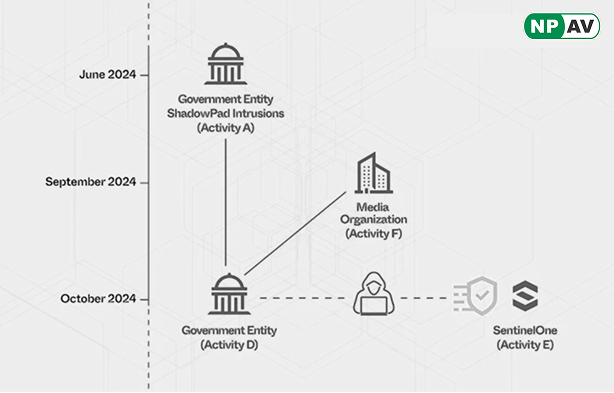
SentinelOne researchers discovered six different activity clusters dating back to June 2024, starting with the compromise of a South Asian government entity. These clusters include:
Activity A: Intrusion into a South Asian government entity (June 2024)
Activity B: Global intrusions targeting various organizations (July 2024 - March 2025) Activity C: Intrusion into an IT services and logistics company (early 2025) managing hardware logistics for SentinelOne employees.


Activity D: Second intrusion into the same South Asian government entity (October 2024)
Activity E: Reconnaissance activity targeting SentinelOne servers (October 2024) Activity F: Intrusion into a leading European media organization (late September 2024) The initial attack on the South Asian government entity involved the deployment of ShadowPad malware obfuscated with ScatterBrain. This ShadowPad activity is linked to recent campaigns delivering the NailaoLocker ransomware after exploiting Check Point gateway devices.
The same government entity was later targeted with a Go-based reverse shell called GoReShell, using SSH for connection. GoReShell was also used in the attack on the European media organization.
Notably, the attackers used tools developed by The Hacker's Choice (THC), marking the first known instance of state-sponsored actors using THC's software.

SentinelOne attributes Activity F to a China-nexus actor loosely affiliated with UNC5174, an "initial access broker" tracked by Google Mandiant. UNC5174 has been linked to exploiting SAP NetWeaver flaws to deliver GOREVERSE, a GoReShell variant.
The threat actors leveraged ORB network infrastructure, likely operated from China, and exploited CVE-2024-8963 and CVE-2024-8190 vulnerabilities to gain an initial foothold before the vulnerabilities were publicly disclosed. UNC5174 is suspected of transferring access to other threat actors after compromising these systems.






