Fake Google Meet Errors Used in ClickFix Campaigns to Spread Infostealing Malware

A new ClickFix campaign is targeting users with fake Google Meet conference errors, luring them to download infostealing malware on both Windows and macOS systems. The campaign impersonates technical issues and prompts victims to run malicious PowerShell code, infecting devices with malware like Stealc, Rhadamanthys, and AMOS Stealer.
- ClickFix Tactic: The campaign uses social-engineering tactics, impersonating Google Meet conference errors to lure victims into running malware-laden PowerShell scripts.
- Evolving Threat: First identified in May, the ClickFix campaign has expanded to target more platforms and regions, including the United States and Japan.
- Target Audience: The campaign primarily focuses on transport, logistics, and corporate environments using virtual meeting platforms like Google Meet.
- Malware Payloads: Victims are infected with various infostealing malware, including Stealc and Rhadamanthys on Windows, and AMOS Stealer on macOS.
- Fake URLs: The malicious campaign mimics legitimate Google Meet URLs to trick users into visiting fake conference pages, delivering malware through fraudulent pop-ups.
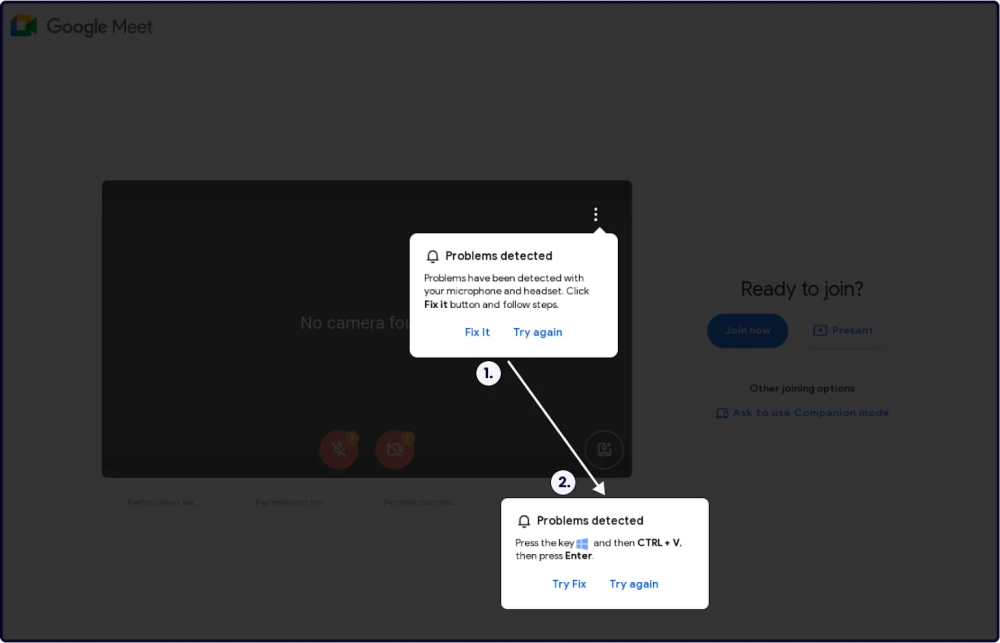
- Broad Targets: In addition to Google Meet, similar fake pages have been detected for Zoom, PDF readers, web3 browsers, and messenger apps, broadening the scope of the attacks.
The ClickFix campaign shows the rising sophistication of social engineering tactics, with attackers leveraging fake Google Meet conference pages to infect users with dangerous malware. As virtual meetings become integral in business operations, users must remain vigilant when clicking on conference links, ensuring they verify URLs and avoid running unsolicited scripts or commands. Companies should employ endpoint security solutions like NPAV to mitigate the risks of malware infection and stay protected against evolving cyber threats.






