Google Forms Turned Phishing Trap: Cybercriminals Exploit Trust to Steal Credentials

Cyber attackers are now weaponizing Google Forms—an otherwise legitimate tool—to craft highly convincing phishing campaigns that evade email security filters and steal user logins. Trusted domains and smart obfuscation tactics make these threats harder to detect and more dangerous than ever.
- Attackers are exploiting the legitimacy of the Google domain (*.google.com) to bypass traditional email security mechanisms.
- Phishing emails pose as urgent security notifications, redirecting users to malicious Google Forms that impersonate login pages of services like Microsoft 365, banking portals, or corporate VPNs.
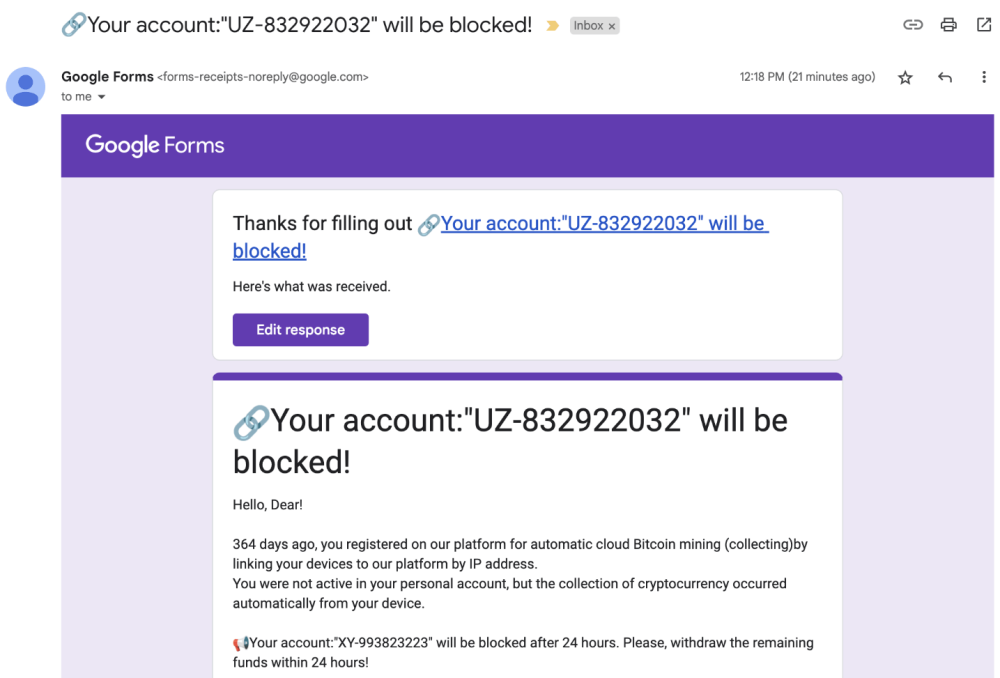
- Google Forms-based links use HTTPS encryption and domain masking, making them appear trustworthy while escaping detection by URL filtering tools.
- Some forms employ webhook-based HTTP POST methods to silently transmit stolen credentials to remote attacker-controlled servers.
- URL shorteners and obfuscation techniques are used to hide the true destination of phishing links within the emails.
- Attacks have surged across financial sectors and educational institutions, with a 63% rise in Google Forms phishing targeting bank customers and students alike.
- Traditional security methods like domain blacklisting struggle to counteract these threats without causing business disruption.
Recommended Security Measures:
- Use advanced email security tools with deep content inspection.
- Enforce SPF, DKIM, and DMARC configurations for outbound and inbound mail validation.
- Enable multi-factor authentication (MFA) on all user accounts.
- Conduct cyber hygiene and awareness training focusing on phishing detection and safe form usage.
- Educate users to verify URLs manually and avoid submitting credentials via Google Forms unless explicitly verified.
As attackers increasingly misuse trusted platforms like Google Forms, cybersecurity requires a proactive approach. Organizations must go beyond standard filtering and empower users with awareness and tools to identify deceptive threats. Trust no link—verify before you click, especially when credentials are at stake.
Comment(s)






