New Stego Campaign Hides AsyncRAT in Images via MS Office Exploit

A stealthy new cyberattack campaign is using steganography and a legacy Microsoft Office vulnerability to deliver AsyncRAT — a powerful remote access trojan capable of full system compromise.
This multi-stage campaign cleverly embeds malicious code in innocent-looking image files, using advanced evasion tactics to bypass traditional security solutions.
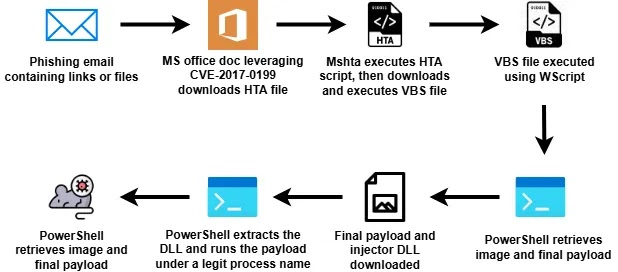
- Attackers are exploiting the CVE-2017-0199 vulnerability in Microsoft Office to launch the infection chain via phishing emails.
- Victims who open the malicious Office documents unknowingly trigger a remote HTA script, which downloads a trojanized Prnport.vbs Windows script.
- This script runs a heavily obfuscated PowerShell command that downloads an image file containing hidden malicious code.
- The malware uses steganography to embed a malicious DLL inside the image, invisible to standard file scans.
- The PowerShell script identifies Base64-encoded segments inside the image and extracts a DLL named Microsoft.Win32.TaskScheduler.
- The injected DLL performs process hollowing, replacing the memory of a legitimate MSBuild.exe process with the AsyncRAT payload.
- AsyncRAT establishes contact with C2 server at 148.113.214.176:7878, granting attackers full remote access to the infected device.
- Attack capabilities include keylogging, remote desktop, surveillance, and secondary payload delivery, including ransomware.
This campaign demonstrates how threat actors are combining old exploits with new evasion strategies like steganography to stay ahead of detection systems. Organizations must prioritize patch management, disable legacy scripting features, and inspect image files for suspicious activity. At Net Protector Cyber Security, we continuously update our defense mechanisms to detect even the most deceptive malware hiding in plain sight.






