RansomHub Ransomware: Sophisticated Malware Attacks Target Corporate Networks

A newly surfaced ransomware group, RansomHub, is aggressively targeting corporate environments using an advanced, multi-stage infection chain that combines initial access malware with strategic network infiltration tactics. Cybersecurity researchers warn that this Ransomware-as-a-Service (RaaS) group poses a serious threat to global organizations by leveraging deceptive update prompts and stealthy backdoors.
- RansomHub is actively advertised on the Dark Web's RAMP forum, offering criminal services tailored for high-profile attacks.
- SocGholish (FakeUpdates) malware is used as the initial infection vector, masquerading as fake browser update notifications on compromised websites.
- Upon execution, SocGholish collects system information, then deploys a python-based backdoor to deepen infiltration if the target is deemed valuable.
- The infection begins via a compromised WordPress site, where victims are tricked into downloading a malicious "Update.zip" archive.
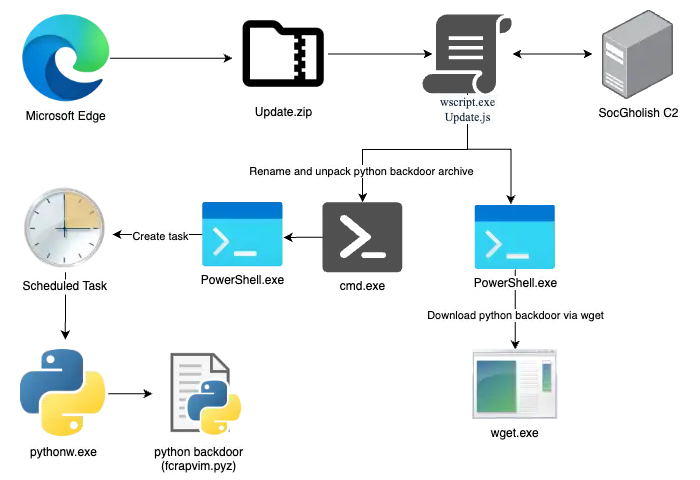
- The zip file contains an obfuscated JScript loader, which communicates with command and control (C2) servers to dynamically retrieve the next payload.
- Persistence is achieved using ActiveX objects and continuous C2 communication, ensuring stable access to compromised systems.
- System reconnaissance is performed using native LOLBin commands, such as "net use" and "systeminfo," to gather intelligence.
- High-value targets are selected based on the reconnaissance data, after which a python-based backdoor establishes a SOCKS proxy for lateral movement.
- Esentire’s Threat Response Unit has confirmed RansomHub’s methodical approach, including a 6.5-minute tactical evaluation window before full deployment.
The emergence of RansomHub highlights the evolving sophistication of modern ransomware operations, blending traditional phishing tactics with highly customized post-infection strategies. Organizations must remain vigilant, regularly patch vulnerabilities, monitor web traffic anomalies, and implement endpoint detection solutions to defend against stealthy threats like SocGholish and RansomHub’s tailored attacks.






