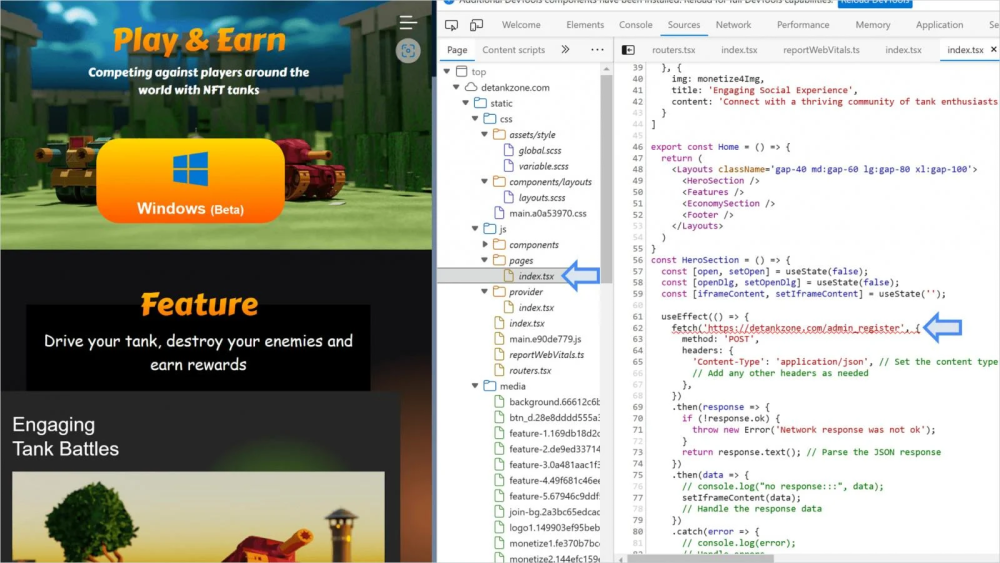
Lazarus Hackers Exploit Google Chrome Zero-Day with Fake DeFi Game to Steal Cryptocurrency Data

The Lazarus hacking group exploited a Google Chrome zero-day vulnerability (CVE-2024-4947) through a fake decentralized finance (DeFi) game, "DeTankZone," targeting individuals in the cryptocurrency sector. This attack demonstrates Lazarus' evolving tactics, using browser exploits and rebranded games to steal sensitive data and potentially cryptocurrency.
- Lazarus Group Attack: Leveraged fake DeFi game, "DeTankZone," to exploit a Google Chrome zero-day vulnerability (CVE-2024-4947).
- Chrome Zero-Day Exploit: The attack used a hidden script to exploit Chrome's V8 engine, gaining access to cookies, authentication tokens, and saved passwords.
- Targeted Cryptocurrency Users: Victims were likely chosen for their involvement in the cryptocurrency space.
- Reconnaissance via Shellcode: Attackers used shellcode to collect system information and determine the value of compromised systems.
- Game as Decoy: The malicious game was rebranded from stolen source code of the legitimate DeFiTankLand game.
- Google Patch Released: Google patched the CVE-2024-4947 vulnerability with Chrome version 125.0.6422.60/.61 in May 2024.
Lazarus' exploitation of the Google Chrome zero-day vulnerability via a fake DeFi game is a stark reminder of the sophisticated and evolving tactics used by cybercriminals to target high-value individuals, particularly in the cryptocurrency space. Organizations and users involved in cryptocurrency trading and investment must stay vigilant by keeping software updated, implementing browser security measures, and using comprehensive cybersecurity solutions to guard against such advanced threats. Net Protector Cyber Security products offer robust protection against browser-based vulnerabilities, phishing campaigns, and advanced persistent threats like those leveraged by the Lazarus group. Stay protected and secure your digital assets with advanced security solutions.






