Phishers Exploit Google Apps Script to Bypass Security Filters and Steal Credentials

Google’s trusted scripting platform is the latest weapon in phishing arsenals, helping attackers craft convincing credential-stealing campaigns that evade traditional email filters.
Cybercriminals are leveraging Google Apps Script, a legitimate tool in Google’s Workspace suite, to host phishing pages that appear trustworthy to both users and security systems. According to research by Cofense, attackers are disguising these pages as authentic login portals to trick users into submitting their credentials — all while operating under the umbrella of a trusted Google domain.
- Phishing emails often masquerade as invoices or tax-related requests, leading victims to click on a malicious link hosted via Google Apps Script.
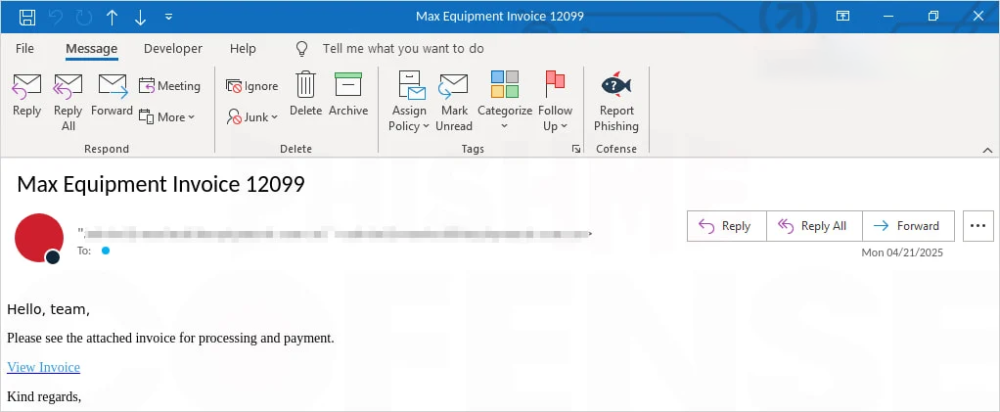
- Google Apps Script runs under the domain script.google.com, which is whitelisted by many organizations, allowing phishing emails to bypass detection.
- Once on the fake login page, victims are prompted to enter credentials, which are silently sent to the attacker’s server in the background.
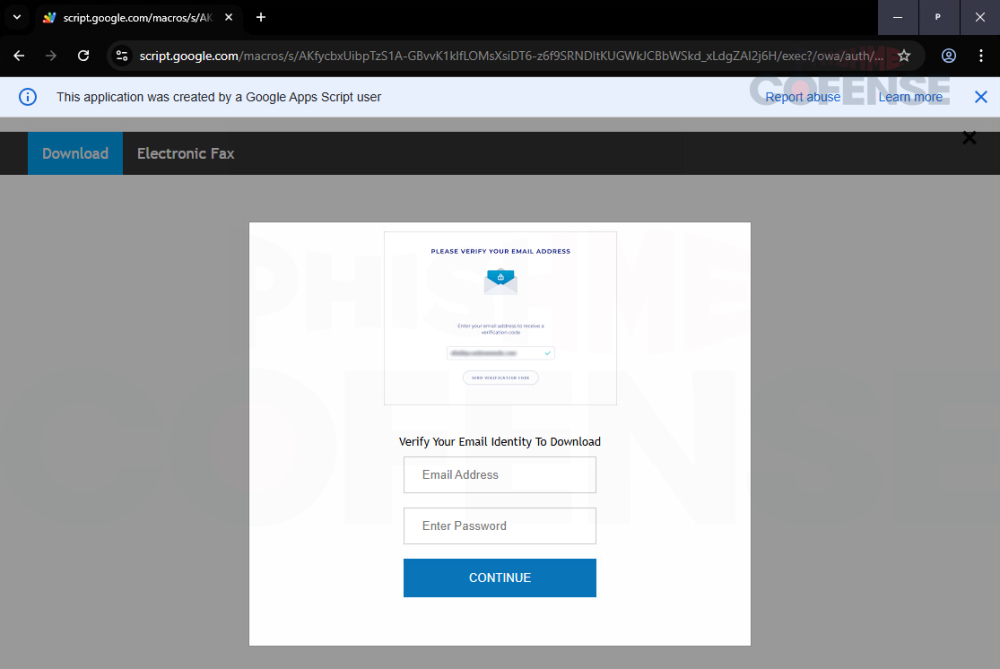
- After the data is harvested, the user is redirected to the real service’s login page to avoid suspicion and delay discovery.
- The attacker can remotely update the phishing content without resending links, making this technique more persistent and harder to block.
- This method exploits the inherent trust in cloud service domains and the wide usage of Google Workspace, which adds legitimacy to the phishing attempt.
This new phishing tactic underscores the danger of platform abuse by cybercriminals who exploit trusted domains to cloak malicious activity. As Google Apps Script becomes the latest tool in their arsenal, it’s critical for organizations to rethink their email and link-filtering strategies.
At Net Protector Cyber Security, we advise:
- Blocking or flagging access to suspicious cloud service URLs like script.google.com
- Training employees to verify the source of emails and double-check invoice links
- Implementing advanced email threat detection systems that go beyond domain trust
In the modern cyber threat landscape, trust is the new attack surface — and no platform is immune.






