Phishers Exploit Google OAuth & DKIM to Deliver Fake Emails That Pass as Legitimate

A sophisticated phishing technique has been uncovered where attackers abuse Google’s OAuth system and DKIM verification to send emails that appear to come from no-reply@google.com, but actually lead users to fake support portals aimed at credential theft.
- Attackers exploit Google OAuth and DKIM replay to deliver emails that pass all security checks.
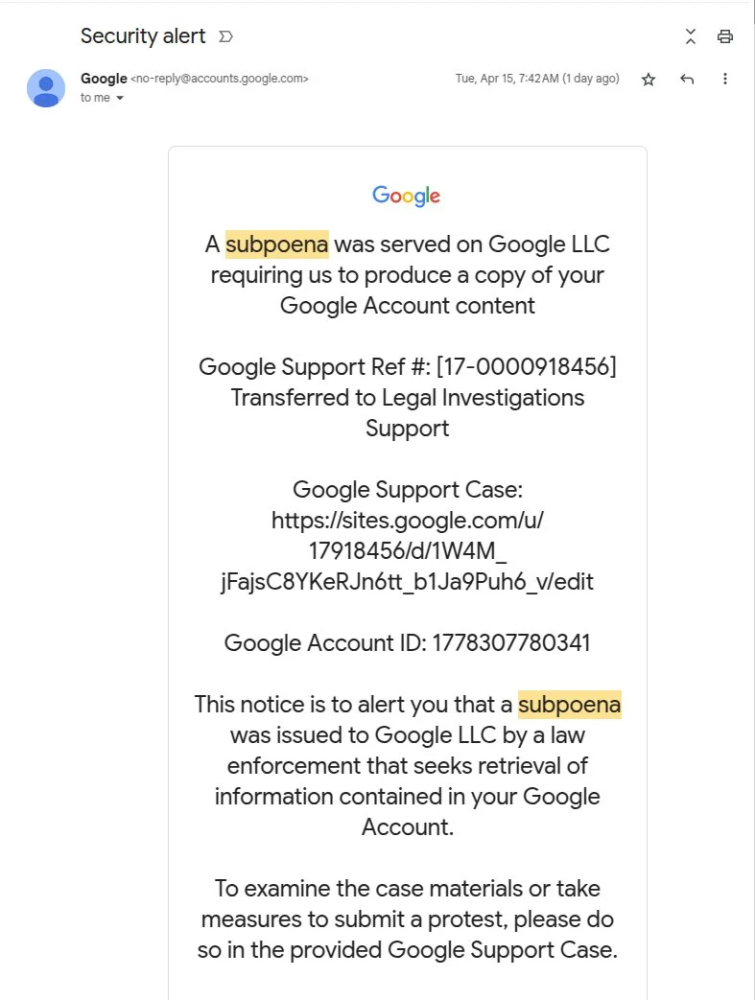
- Emails appear to be legitimate Google security alerts, even blending seamlessly into users’ inboxes alongside real messages.
- The phishing email links to a fake Google support portal hosted on sites.google.com, making it look authentic.
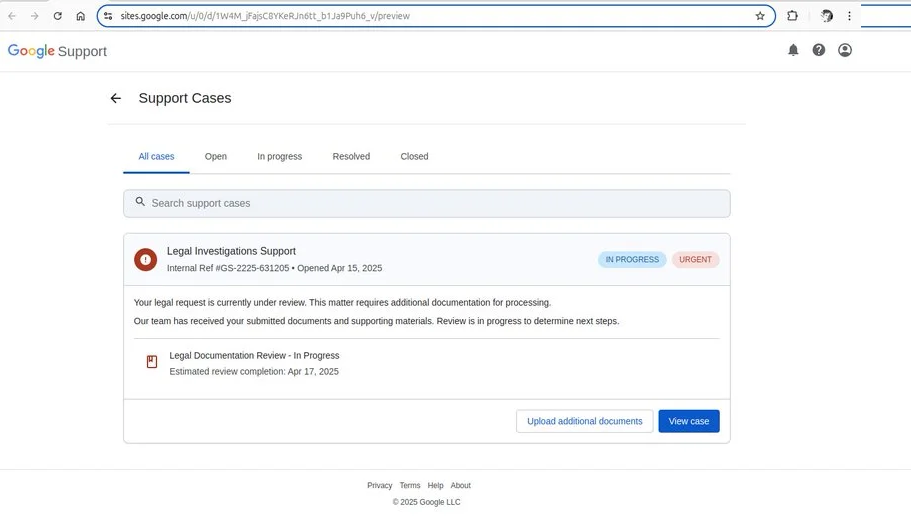
- The fraudulent message is signed with a valid Google DKIM key, bypassing email authentication filters.
- The attacker registers a Google account with an address like me@maliciousdomain.com and uses the OAuth app name as the phishing message itself.
- Google automatically sends a security alert after OAuth access is granted—this alert is forwarded to victims and passes all authenticity checks.
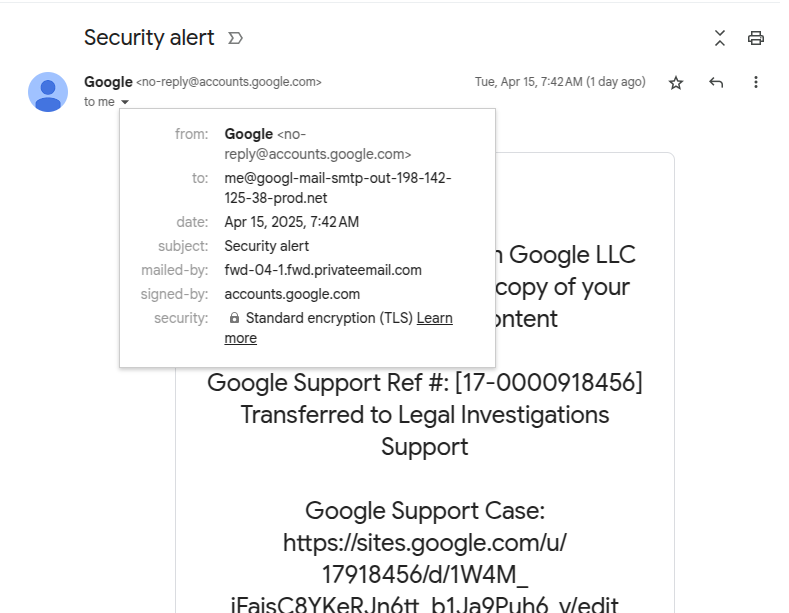
- Gmail UI displays the forged email as if it’s addressed to the recipient, thanks to the clever use of the “me@” email handle.
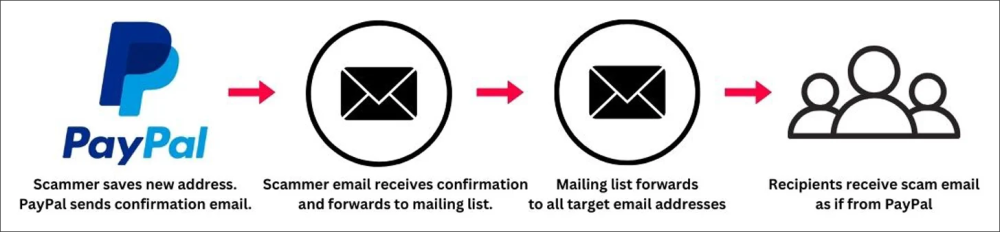
- Similar DKIM abuse tactics have been observed with PayPal, using their “gift address” feature to relay phishing emails through PayPal’s servers.
- Despite initially claiming the system was functioning as intended, Google has now acknowledged the risk and is working on a fix.
This DKIM replay phishing attack reveals a dangerous blind spot in trusted infrastructure. When cybercriminals can weaponize security alerts from platforms like Google and PayPal, even tech-savvy users are at risk. Organizations and individuals must remain cautious, double-check URLs, and never enter credentials unless on the official domain. Net Protector advises all users to enable two-factor authentication and deploy advanced anti-phishing solutions to stay ahead of such evolving threats.






