Remote Methods RCALL.EXE
1. Start > Run > Remote : RCALL.EXE launches
a.Step first Win+R enter
Exe name, File Size and Icon of 3 exe :
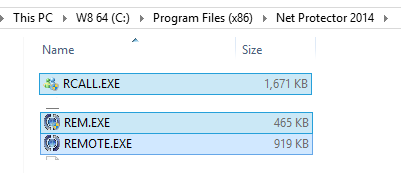
- rem.exe :
Launches remote.exe and rcall.exe - remote.exe :
919kb Actual Remote EXE TV - rcall.exe :
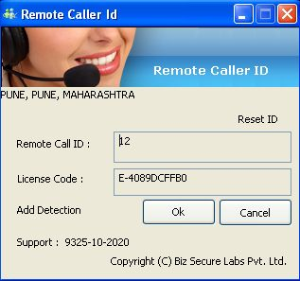
Ask user for Remote Caller ID and sends the Report to Rcall Server
Add S1234 for SSO Lab Rcall Server
http://115.115.124.178/
b. step second (this is rcall.exe)
a. Step first lauch NPAV dashboard.
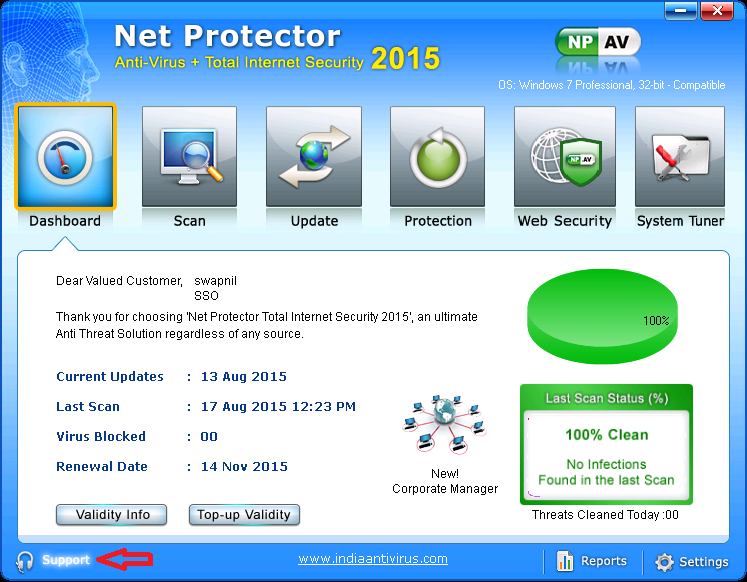
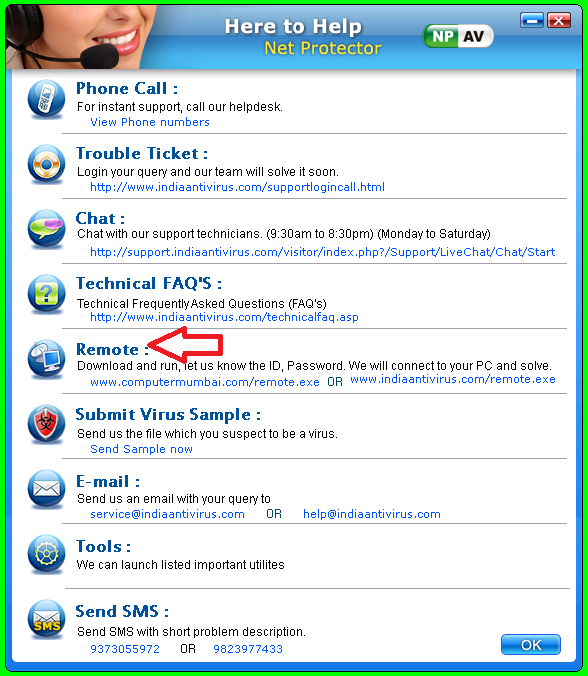
3. Right Click Emailscn > Contact Helpdesk.
a.Step first right click on Emailscn Red Tray ICON.
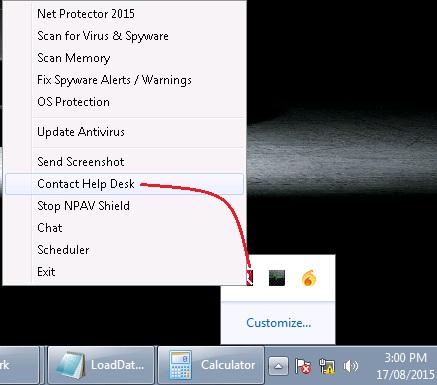
b.Step second click on Remote Support (TECHNICALHELPDESK.EXE) BG
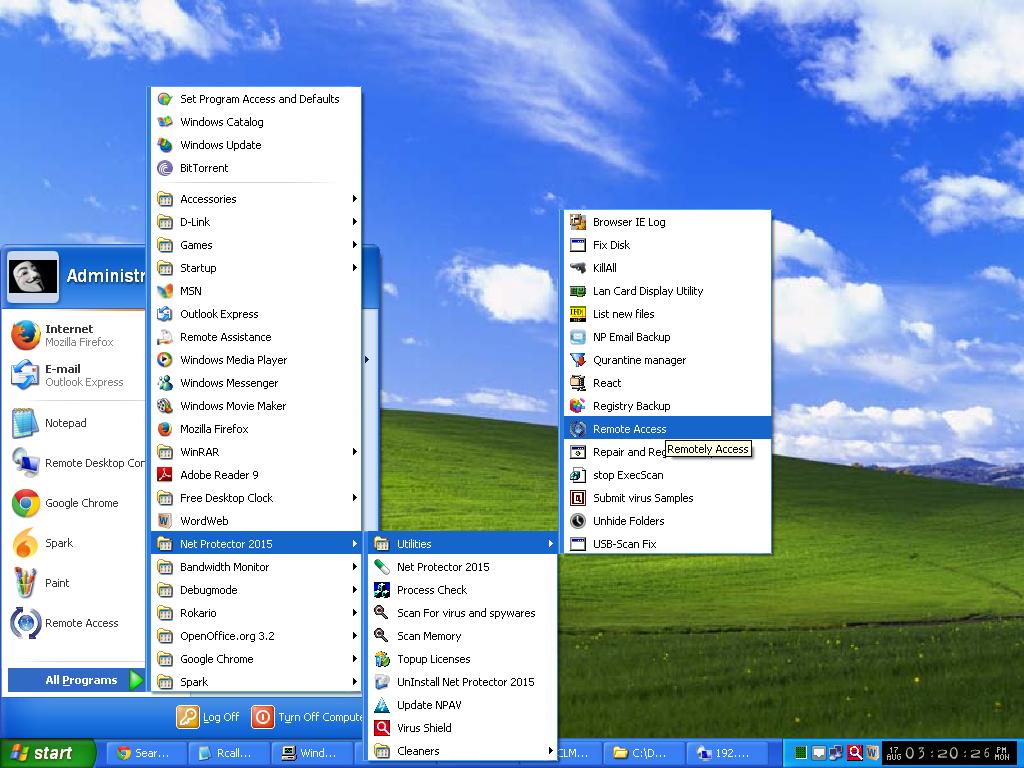
4. Windows Start Menu > Remote Access - * in this option rcall.exe is not launched
Point "Remote Access"
to rem.exe
Winodws XP
Start > All Programs > Net Protector > Utilities > Remote Access
LNK in Start Menu :
C:\Documents and Settings\All Users\Start Menu\Programs\Net Protector 2015\Utilities\Remote Access.lnk
Target
"C:\Program Files\Net Protector 2015\REMOTE.EXE"
Check on Windows XP, Win7, Windows 8.0, 8.1, Win10
5. From WebSite : * in this option rcall.exe is not launched
http://www.computermumbai.com/
sixth no. option For Remote Support, Save to Desktop and Run.
Download and Run
Remote.exe






