Ymir Ransomware: A New Breed of Memory-Based Attacks Targeting Corporate Networks

A new ransomware strain, Ymir, is causing alarm with its unique memory exploitation tactics to evade detection. This advanced ransomware, following an initial breach via RustyStealer malware, recently hit a corporate network in Colombia, signaling the growing complexity and sophistication of ransomware strategies that target high-value corporate credentials.
- Memory Manipulation: Ymir ransomware uses memory functions (malloc, memmove, memcmp) for in-memory code execution, enhancing stealth and avoiding traditional detection.
- Chain Attack with RustyStealer: The attack started with RustyStealer malware to steal corporate credentials, which were then used to deploy the ransomware.
- Customizable Targeting: The ransomware supports selective encryption, allowing attackers to choose file paths and whitelist files.
- Tools and Techniques: Threat actors installed Advanced IP Scanner, Process Hacker, and SystemBC malware scripts to enable remote exfiltration.
- Encryption Protocol: Ymir uses ChaCha20 for file encryption, appending a unique extension to encrypted files.
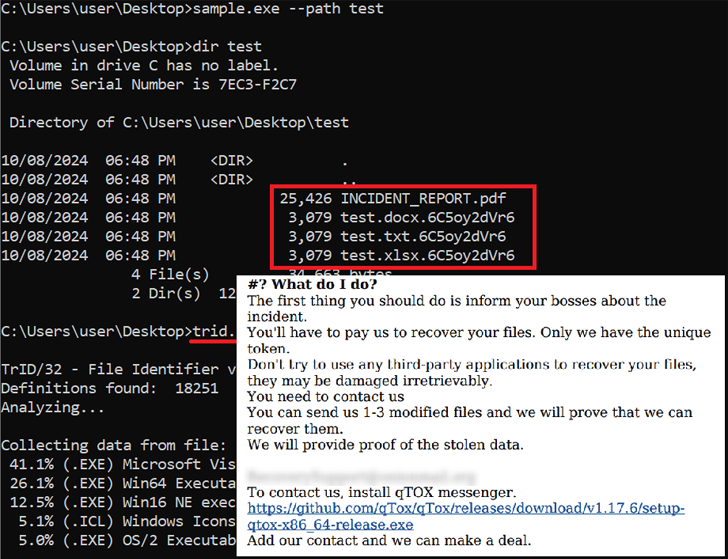
- Trends in Attack Strategies: Tactics like leveraging Quick Assist and malspam campaigns are part of a broader strategy to gain unauthorized access.
- Rise in Ransomware Groups: Reports show a 30% rise in ransomware groups, signaling increased fragmentation but not necessarily a rise in overall victim numbers.
- Evolving Threat Landscape: Politically motivated ransomware use by hacktivist groups, and recent calls to limit ransom payment insurance, highlight the complex dynamics within the ransomware ecosystem.
Ymir ransomware’s advanced memory management tactics underscore the evolving sophistication in ransomware attacks on corporate networks. By using credential-stealing malware as a gateway, attackers now create tailored attacks that exploit unpatched systems and leverage insider tricks, such as impersonating IT support. As ransomware groups diversify, organizations need vigilant monitoring, advanced threat detection, and effective vulnerability management to counter this persistent threat.






