Thousands of Fake Shopping Sites Launched to Steal Credit Card Data During Black Friday

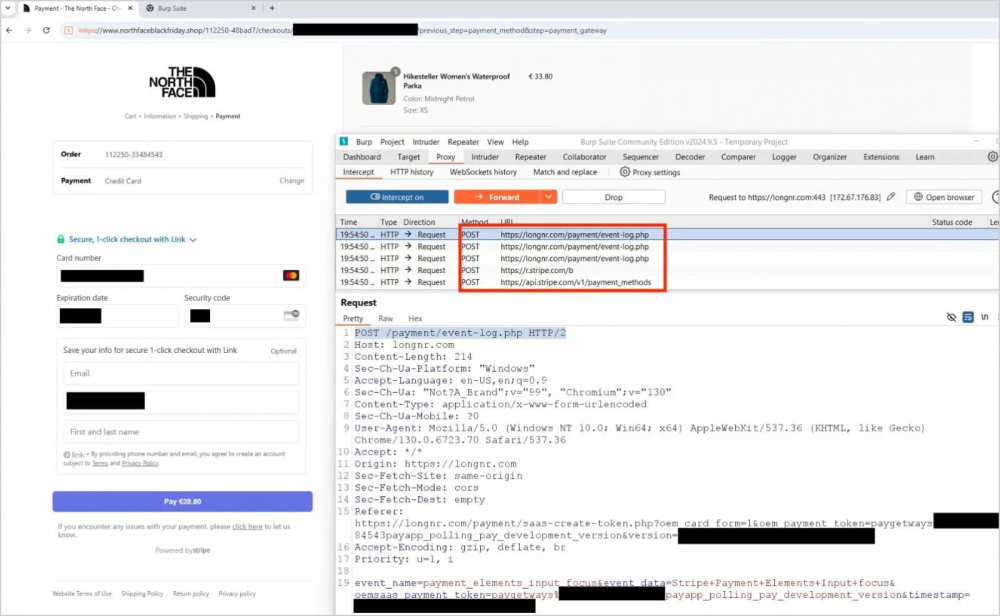
A new fraud campaign led by the Chinese threat actor SilkSpecter is leveraging 4,700 fake e-commerce websites to steal payment card details and personal information. These sites mimic popular brands and utilize legitimate payment processors like Stripe to deceive victims.
Threat Actor Details:
- The Chinese group SilkSpecter is behind the campaign.
- Operates 4,695 fake domains targeting U.S. and European shoppers.
Targets and Tactics:
- Impersonates major brands like North Face, IKEA, Lidl, and more.
- Promotes Black Friday discounts to lure unsuspecting buyers.
- Utilizes legitimate payment processors (e.g., Stripe) for credibility.
Phishing and Data Theft:
- Collects credit/debit card details, expiration dates, CVV codes, and phone numbers.
- Information is sent to attacker-controlled servers for misuse.
- Uses phone numbers for subsequent voice or SMS phishing.
Technical Tools and Indicators:
- Domains commonly use ".shop," ".store," ".vip," or ".top" extensions.
- Leverages Google Translate for language adjustments based on victim location.
- Tracks visitor behavior using tools like OpenReplay, TikTok Pixel, and Meta Pixel.
Attribution and Evidence:
- Indicators of Chinese origin include IP addresses, ASNs, domain registrars, and code.
- Previously used Chinese SaaS platforms for operations.
Safety Recommendations for Shoppers:
- Shop only on official brand websites.
- Avoid clicking on ads, social media links, or unverified search results.
- Use multi-factor authentication and monitor financial account activity regularly.
0 Comment(s)






