Chinese Botnet 'Raptor Train' Infects 260,000 Devices, Targeting Critical Infrastructure

A new cybersecurity alert reveals that a Chinese state-sponsored botnet, dubbed “Raptor Train,” has compromised more than 260,000 devices, including SOHO routers, IP cameras, NVRs, and NAS devices. The botnet has targeted critical infrastructure in the US, Taiwan, and other regions, with a primary focus on military, government, and industrial sectors.
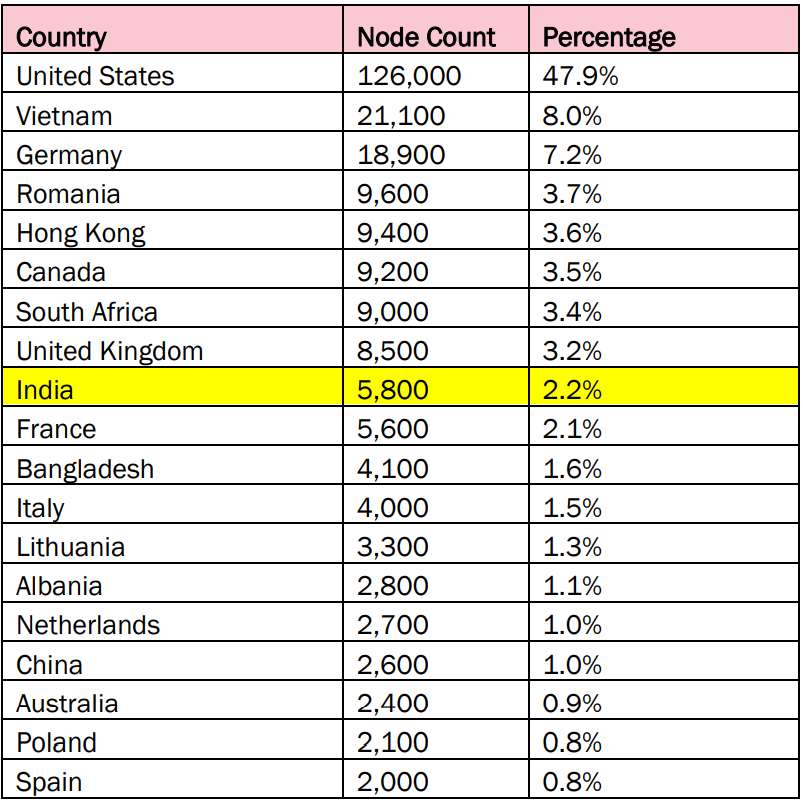
Botnet Overview:
-
- Raptor Train: A multi-tiered, enterprise-grade botnet that has grown significantly since its inception in May 2020. It mainly infects routers, modems, IP cameras, and NAS devices, with compromised systems peaking at over 60,000 active devices in a single campaign.
- Targets: The botnet has been used to target US and Taiwanese entities in the military, government, higher education, telecommunications, and IT sectors.
Primary Payload: Mirai Variant:
-
- Raptor Train uses a Mirai malware variant, referred to as "Nosedive," typically used for distributed denial-of-service (DDoS) attacks.
- Though equipped for DDoS, Raptor Train hasn't been observed conducting such attacks, indicating that the operators may have other malicious intentions.
Flax Typhoon Connection:
-
- The FBI has linked the botnet to Flax Typhoon, a Chinese state-sponsored hacking group, which used the botnet to target critical infrastructure.
- The operators control Raptor Train through the Chinese company Integrity Technology Group, using China Unicom’s Beijing Province Network IP addresses.
Disruption by the FBI:
-
- The FBI and cybersecurity researchers successfully disrupted the botnet, issuing commands to remove the malware from thousands of infected devices.
- The FBI retrieved 1.2 million records of compromised devices from a MySQL database on the botnet’s management server.
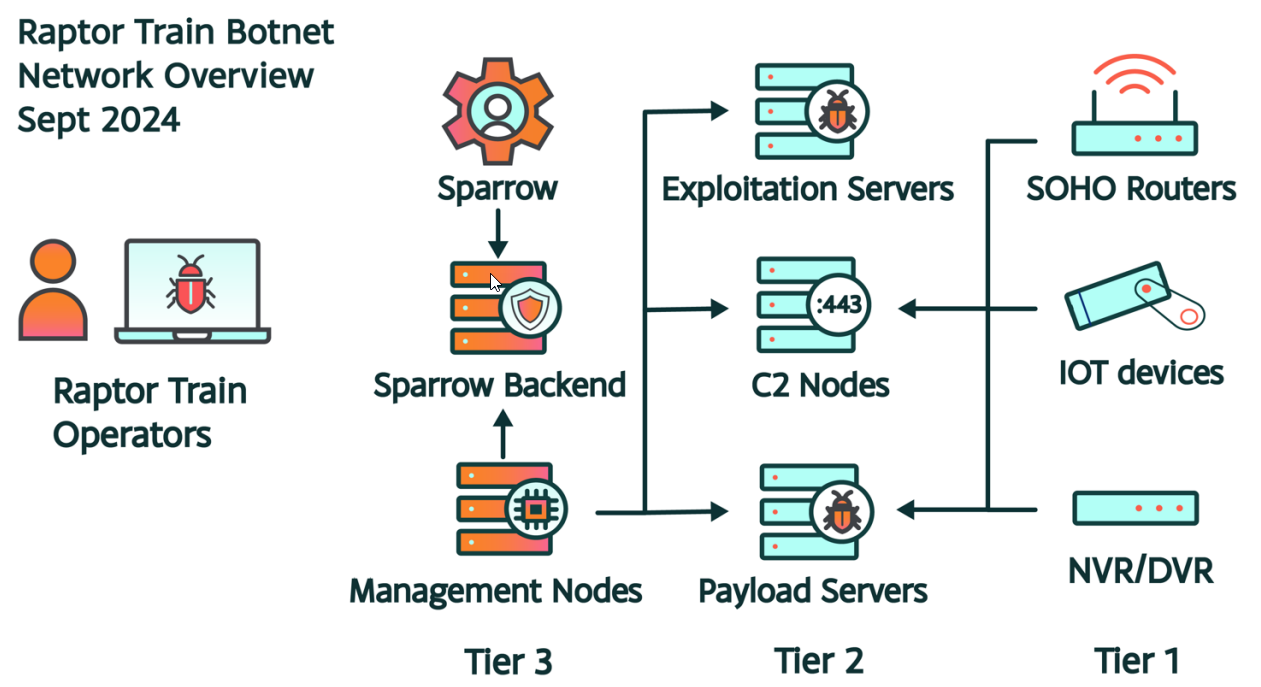
Complex, Multi-Tiered Structure:
-
- The botnet is organized into three tiers:
- Tier 1: Infected devices, including modems, routers, and IP cameras, used for initial infection.
- Tier 2: Command and control (C2) servers that manage payloads and exploitation servers.
- Tier 3: Sparrow nodes, which provide management interfaces and backend functions for controlling the botnet.
- The operators manually control the botnet using SSH and TLS connections from Tier 3 systems.
- The botnet is organized into three tiers:
Campaigns and Zero-Day Exploits:
-
- Raptor Train has launched multiple campaigns since 2020, with the most recent campaigns, Canary and Oriole, adding thousands of new devices to the botnet.
- The botnet operators exploit over 20 device types using both zero-day and known vulnerabilities.
Targets and Global Reach:
-
- The botnet has been involved in exploitation attempts against US military and government entities, IT providers, and defense contractors.
- In addition to US targets, the botnet was used to attack a government agency in Kazakhstan and organizations in the defense sectors of other countries.
Defensive Measures:
-
- For Network Admins:
- Monitor for large outbound data transfers.
- Look out for suspicious traffic to known Raptor Train infrastructure points.
- For Consumers:
- Regularly reboot routers and install vendor updates.
- Replace outdated, unsupported devices that no longer receive security patches.
- For Network Admins:
Raptor Train’s wide-reaching impact demonstrates the sophistication of state-sponsored botnets. By targeting critical infrastructure across the globe, attackers aim to disrupt national security and industrial sectors. Proactive monitoring and maintaining updated systems are essential steps in defending against such threats.






