Phishing Scam Alert: Hackers Swap 'm' for 'rn' to Fake Microsoft and Steal Your Logins
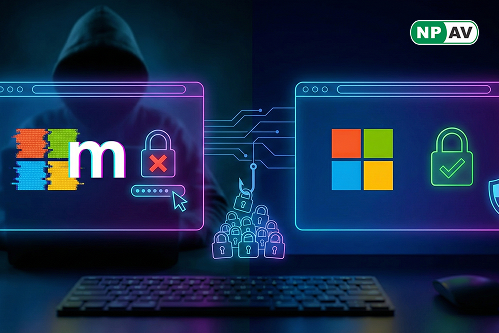
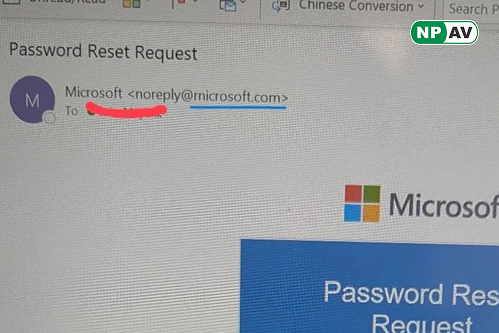
In a clever phishing scam, cybercriminals are duping users by swapping the 'm' in "Microsoft.com" with 'rn', creating "rnicrosoft.com." This typosquatting exploit relies on font kerning to make the fake domain look identical to the real one at a glance—especially on mobile screens where URLs get truncated.

The attack mimics official Microsoft emails, complete with logos and layouts, tricking people into clicking malicious links or sharing credentials. It's part of a broader trend in homoglyph attacks, where letters are replaced to fool the eye.
Common Typosquatting Tricks
Letter Combo: 'rn' for 'm' (e.g., rnicrosoft.com).
Number Swap: '0' for 'o' (e.g., micros0ft.com).
Hyphenation: Adding subdomains like microsoft-support.com.
TLD Switch: Using .co instead of .com.

How to Stay Safe
Don't rely on filters—check the full sender address, hover over links to reveal the real URL, and inspect email headers. For password resets, ignore links and go directly to the official site. Train your team to spot these deceptions before clicking.
Stay vigilant; these subtle tricks are getting smarter. What phishing tactics have you encountered? Share in the comments!
NPAV offers a robust solution to combat cyber fraud. Protect yourself with our top-tier security product, Z Plus Security






