Critical Notepad++ Vulnerability Exposes Users to System Compromise

A serious privilege escalation vulnerability has been identified in Notepad++ version 8.8.1, potentially putting millions of users at risk of complete system compromise. Designated CVE-2025-49144, this flaw allows attackers to gain SYSTEM-level privileges through a technique known as binary planting, with a proof-of-concept (PoC) now publicly available.
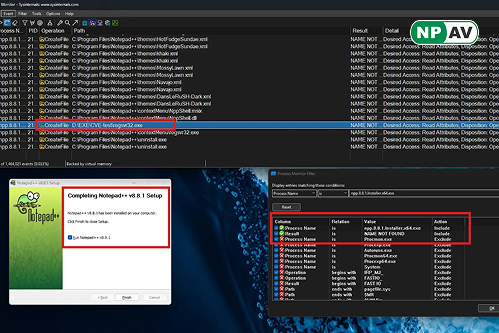
The vulnerability affects the Notepad++ installer released on May 5, 2025, exploiting an uncontrolled executable search path that enables local privilege escalation attacks. Security researchers found that the installer searches for executable dependencies in the current working directory without proper verification, creating an opportunity for malicious code injection.

Attack Methodology
The exploitation process is alarmingly simple. Attackers can place a malicious executable, such as a compromised regsvr32.exe, in the same directory as the Notepad++ installer. When users run the installer, the system automatically loads the malicious file with SYSTEM privileges, granting attackers complete control over the target machine.
The PoC materials include Process Monitor logs that demonstrate the installer’s vulnerability, along with video evidence of successful exploitation. Given Notepad++’s substantial user base—over 1.6 million monthly visits to its official website—this vulnerability poses significant risks, especially in corporate environments.

Mitigation and Response
In response, Notepad++ developers have released version 8.8.2 to address this critical vulnerability, implementing secure library loading practices and absolute path verification for executable dependencies. Users are strongly urged to update immediately to eliminate the security risk.
Security experts recommend additional protective measures, such as running installers from secure directories and maintaining updated endpoint security solutions. This incident highlights the importance of secure software development practices, particularly in installer design and dependency loading mechanisms. As cyber threats evolve, proactive vulnerability management remains essential for widely used software platforms.






