Fast Flux: The Evasive Cyber Technique Powering Malware, Phishing & C2 Networks

Cybersecurity agencies including CISA and FBI have issued a warning about the growing use of a stealthy cyberattack technique called Fast Flux, used by hackers to hide malware servers, enable phishing websites, and build resilient command-and-control (C2) systems.
What is Fast Flux?
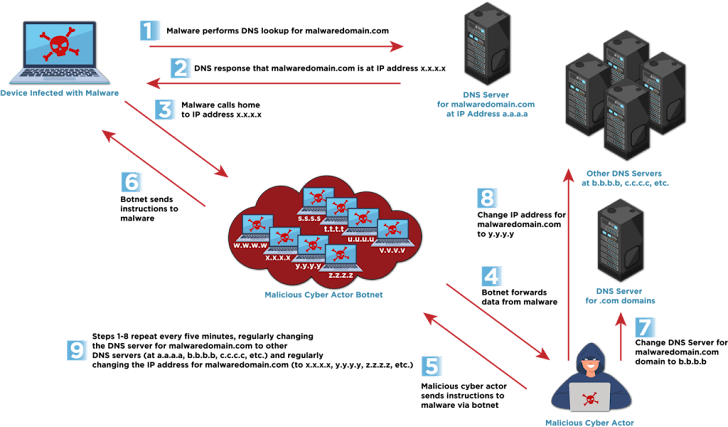
- A method that hides malicious infrastructure by rapidly changing the IP addresses linked to a single domain name using DNS tricks. This makes it extremely difficult to block or track these threats.
Single vs. Double Flux:
- Single Flux: One domain linked to many IPs that rotate quickly.
- Double Flux: The domain’s DNS servers also rotate, adding another layer of stealth.
Used By Advanced Threat Groups:
- Hackers like Gamaredon, CryptoChameleon, and Raspberry Robin are actively using Fast Flux to evade detection and law enforcement takedowns.
More Than Just Malware Hosting:
- Fast Flux is used not only for hiding malware C2 infrastructure but also to host phishing sites and distribute malicious files.
Global Advisory Issued:
- Security agencies from the U.S., Canada, Australia, and New Zealand have jointly issued a warning, calling Fast Flux a national security threat.
Difficult to Block:
- Because Fast Flux uses constantly changing IPs and DNS servers, it bypasses traditional IP blocking and takedown techniques.
Expert Insight:
- While it's a well-known method (first seen in 2007), it still requires significant resources and expertise, making it a tool of choice for serious cybercriminals.
To Stay Protected:
- Block IP addresses and sinkhole malicious domains
- Use threat intelligence tools to monitor suspicious DNS activity
- Filter traffic from domains with poor reputations
- Use advanced cybersecurity solutions that monitor DNS behavior
Fast Flux may be an old trick in the hacker's toolbox, but it's back in action — smarter and stronger. It’s helping cybercriminals hide in plain sight, keeping malware servers alive longer, and increasing the impact of phishing attacks.
Net Protector Cyber Security urges all users and organizations to stay alert, keep security solutions updated, and monitor DNS activity closely to avoid falling victim to these evolving threats.






