Hackers Imitate Microsoft ADFS Login Pages to Steal Credentials
Cybercriminals are using fake Microsoft Active Directory Federation Services (ADFS) login pages to steal usernames, passwords, and MFA codes from employees in education, healthcare, and government organizations. The stolen credentials allow hackers to access corporate email accounts, send phishing emails, and commit financial fraud.
- Hackers are tricking employees into entering their credentials on fake Microsoft ADFS login pages, which look identical to real ones.
- 150+ organizations have been targeted, including those in education, healthcare, and government sectors.
- Emails appear to come from the IT department, asking users to update security settings or accept new policies.
- Fake login pages capture usernames, passwords, and MFA codes, allowing hackers to bypass multi-factor authentication (MFA).
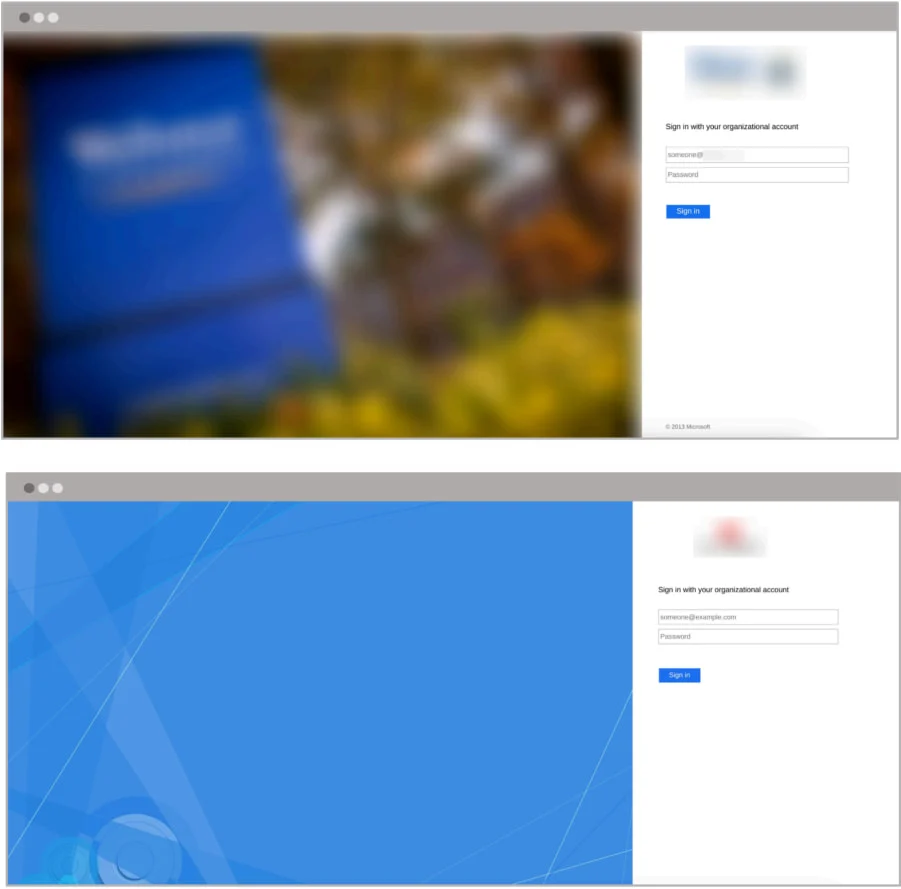
- Stolen credentials are used to hack corporate emails, steal data, create fake email rules, and launch financial fraud attacks like business email compromise (BEC).
- Attackers use VPNs to hide their real location and appear closer to the victim's organization.
- Experts recommend switching to modern security solutions like Microsoft Entra and using advanced email filters to block phishing attempts early.
Hackers are exploiting trust in familiar login pages to steal credentials and gain access to sensitive information. Organizations must train employees to recognize phishing emails, enable stronger security measures, and use AI-powered phishing detection tools like NPAV’s Endpoint Security to prevent cyberattacks before they happen.
Comment(s)






