New TxTag Phishing Scam Uses .gov Domain to Deceive Employees

A sophisticated phishing campaign targeting employees with fake toll payment notices has been uncovered, combining government domain spoofing with social engineering tactics.
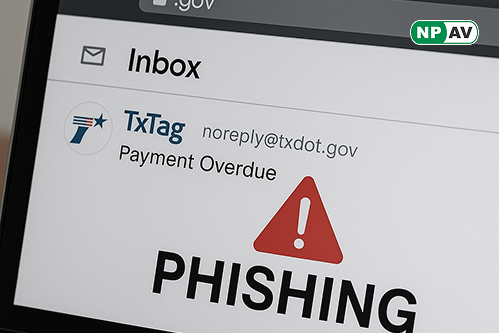
The attackers craft messages that appear to be from TxTag, warning recipients that their accounts are at risk of suspension unless outstanding balances are paid immediately. This campaign leverages urgency and fear to compel victims into clicking malicious links that lead to credential theft.
Deceptive Techniques Enhance Legitimacy
The phishing emails utilize a particularly deceptive technique by employing an actual government delivery system to enhance their legitimacy. The messages seem to originate from official channels, displaying government domains that many security systems would typically trust.

However, there is a critical discrepancy:
while the emails claim to represent Texas toll authorities, they actually use Indiana’s GovDelivery instance, a subtle but significant indicator of the fraud.
Cofense researchers identified this campaign through their Phishing Defense Center (PDC), noting that the attack demonstrates increasing sophistication in how threat actors impersonate trusted entities.
The Phishing Process
When recipients click the embedded link, they are directed to a convincing replica of a TxTag payment portal at “txtag-help[.]xyz,” where a multi-stage information harvesting operation begins. The infection mechanism is a carefully orchestrated sequence designed to maximize data collection while maintaining the illusion of legitimacy.
Initially, victims encounter a welcome page displaying a TxTag logo and a notification of a modest $6.69 outstanding balance. This relatively small amount is strategically chosen to seem plausible and not raise immediate suspicion.

Credential Harvesting Methodology
After proceeding, victims are presented with a form requesting extensive personal information, including full name, email address, phone number, and complete mailing address. Unlike legitimate toll payment systems, this phishing site does not require login credentials, an oversight that security-conscious users might notice.
The attackers’ primary objective becomes clear on the subsequent screen, where victims are prompted to enter complete payment card details, including card number, expiration date, and security code. The campaign employs validation techniques to ensure the quality of harvested data, requiring correct CVV digit counts before allowing form submission.
Upon completion, victims see a fake “Payment is processing” message, potentially followed by an error claiming the card isn’t supported—prompting them to enter additional payment methods and expanding the attackers’ haul of financial credentials.
These tactics exemplify how modern phishing operations combine technical deception with psychological manipulation, bypassing traditional security measures while exploiting human trust in governmental authorities and fear of penalties.






