Tycoon2FA Campaign Exploits Malformed URLs to Hijack Microsoft 365 Accounts

A new phishing campaign weaponizes malformed URLs to bypass email filters and steal Microsoft 365 credentials—even bypassing two-factor authentication.
Researchers have linked the attack to Tycoon2FA, a notorious Phishing-as-a-Service (PhaaS) operation that enables adversary-in-the-middle (AitM) interception of login sessions. The threat actors behind this campaign are using subtle but dangerous techniques to trick both users and security systems.
- Phishing emails contain malformed links using backslashes (https:\$$) instead of forward slashes (https://), evading detection while remaining browser-compatible.
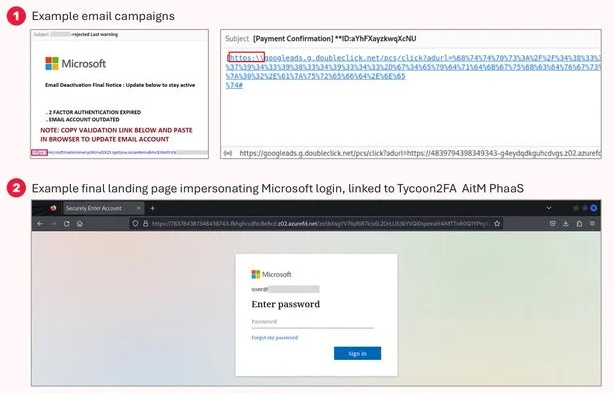
- Victims are redirected through legitimate-looking URLs, some leveraging Azure Front Door and Cloudflare Workers for hosting phishing infrastructure.
- The campaign’s obfuscation methods include URL encoding and redirect chains that obscure the final destination of the malicious site.
- Targets are led to high-fidelity Microsoft login pages designed to harvest login credentials and authentication tokens in real time.
- Tycoon2FA’s AitM capabilities allow attackers to bypass multi-factor authentication, giving them full access to Microsoft 365 accounts.
- The captured credentials grant attackers entry into emails, SharePoint, OneDrive, Teams, and connected services, posing severe risks to corporate data.
- Example of encoded URL redirection used in the attack:
hxxps://googleads.g.doubleclick.net/pcs/click?adurl=%68%74%74%70%73%3A%2F%2F%34%38%33...
This attack demonstrates how attackers are evolving past basic phishing techniques—leveraging browser behavior inconsistencies and cloud infrastructure to avoid detection. Organizations must monitor for malformed URLs and suspicious redirect chains, and users should be trained to critically inspect links, even those that appear legitimate.
Net Protector recommends enhanced URL inspection, DNS traffic monitoring, and proactive phishing simulation training to defend against such advanced phishing threats.






