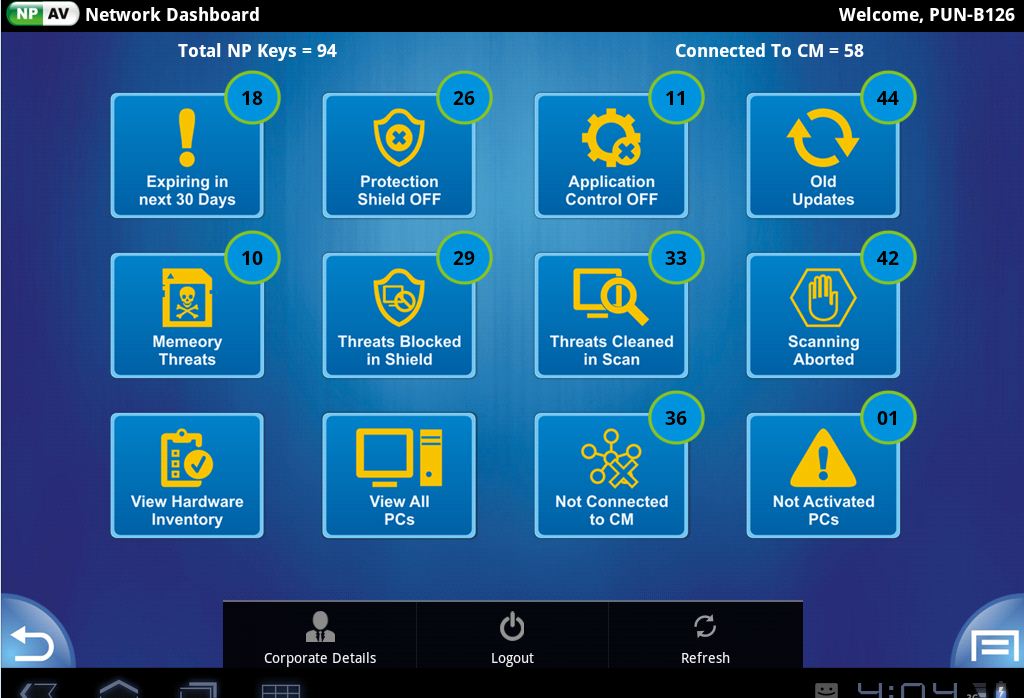
App for Viewing Status of Endpoint Security PCs
Net Protector LAB has developed and released a new Free App for Android Mobile / Tablet.
Administrator or Managers can view security status and reports of entire network from any Smartphone or Tablet from any location.
The List of features of these app : (Search by PC Name)
1) Expiring in next 30 days.
2) Protection shield OFF.
3) Application Control OFF.
4) Old updates.
5) Memory Threats.
6) Threats Blocked In Shield.
7) Threats Cleaned In Scan.
8) Scanning Aborted.
9) View Hardware Inventory.
11) Not Activated PC's
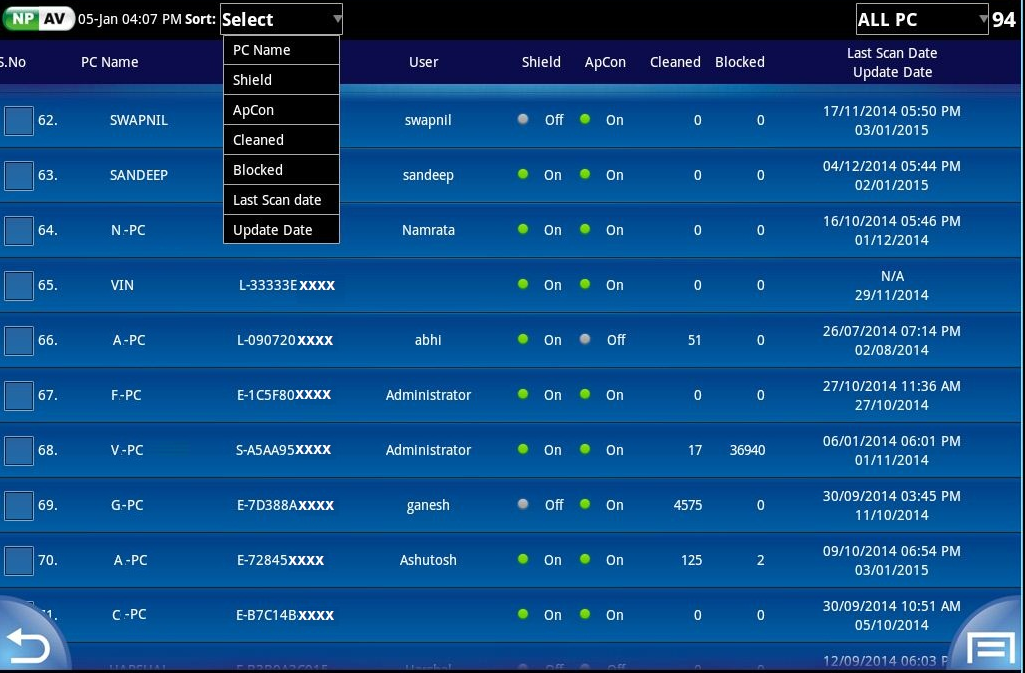
12) View All PC's:
a) Add Comment / View Comment.
b) View virus details :
—> Brow Log.
—> Memory Scan.
—> Installed Softwares.(view in slot of 10 records if more numbers of records are available)
—> LanMon.(view in slot of 10 records if more numbers of records are available)
—> ModV.(view in slot of 10 records if more numbers of records are available)