DarkCloud Stealer v4 Abuses AutoIt Scripts to Evade Detection and Hijack Login Credentials

The latest variant of DarkCloud Stealer uses AutoIt scripting and advanced evasion techniques to target financial, healthcare, and e-commerce sectors. With over 120,000 accounts compromised since March 2025, this malware showcases a dangerous blend of legacy scripting abuse and stealthy credential theft.
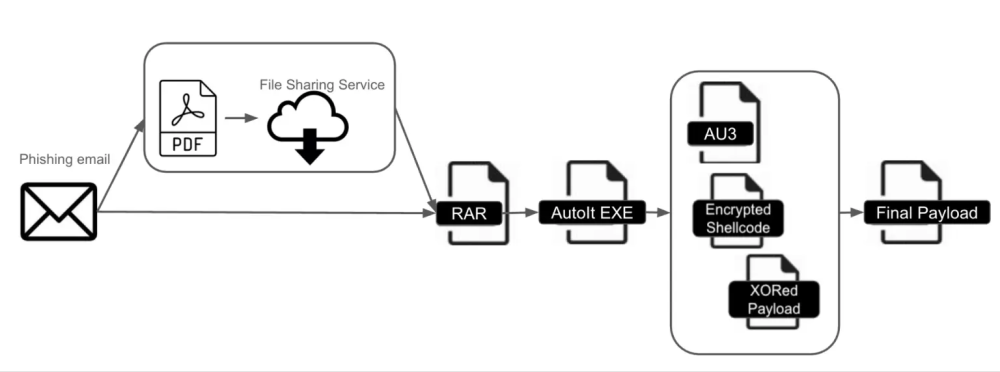
- DarkCloud Stealer v4 first emerged in March 2025, targeting victims across Asia and Europe via phishing emails, malvertising, and fake software updates.
- Utilizes AutoIt, a scripting language for administrative tasks, to compile malicious payloads into standalone executables that mimic legitimate applications.
- Payloads are executed directly in memory, bypassing traditional file-based antivirus and sandbox detection mechanisms.
- Steals browser cookies, autofill data, and 2FA tokens, exfiltrated through HTTPS to attacker-controlled servers.
- Employs Base64 and XOR string obfuscation, along with junk code insertion, to evade static analysis.
- Implements process hollowing by injecting malicious code into legitimate processes like explorer.exe and svchost.exe, enabling stealthy execution.
- Establishes persistence through scheduled tasks and registry entries (HKCU\Software\Microsoft\Windows\CurrentVersion\Run).
- Analysts recorded over 120,000 compromised accounts, with stolen credentials sold on underground forums and darknet markets.
- Threat actors can dynamically update modules, allowing DarkCloud to bypass evolving defenses.
- IOCs include compiled AutoIt scripts (.a3x files), unusual AutoIt-related processes, and outbound connections to domains like malware[.]cc.
DarkCloud Stealer v4 is a clear reminder that attackers are increasingly blending legacy scripting tools with modern evasion techniques. By leveraging AutoIt and process hollowing, this threat avoids standard detection paths while delivering powerful credential theft capabilities. Organizations must focus on behavioral detection, block AutoIt script execution where unnecessary, and educate users to resist socially engineered threats. Proactive monitoring is key to staying ahead of this evolving malware strain.






