Hidden in Plain Sight: Hackers Use JPG Images to Deploy Fully Undetectable Ransomware

Cybercriminals are now leveraging steganography to hide ransomware in ordinary JPG image files, deploying Fully Undetectable (FUD) malware that bypasses traditional security solutions. These advanced tactics exploit metadata and pixel data to deliver multi-stage attacks — silently and effectively.
- Attackers embed obfuscated PowerShell code within the EXIF metadata of JPG images.
- Victims receive these malicious images via email, social media, or compromised websites.
- An Office document with macros acts as a secondary loader to extract and execute the hidden script.
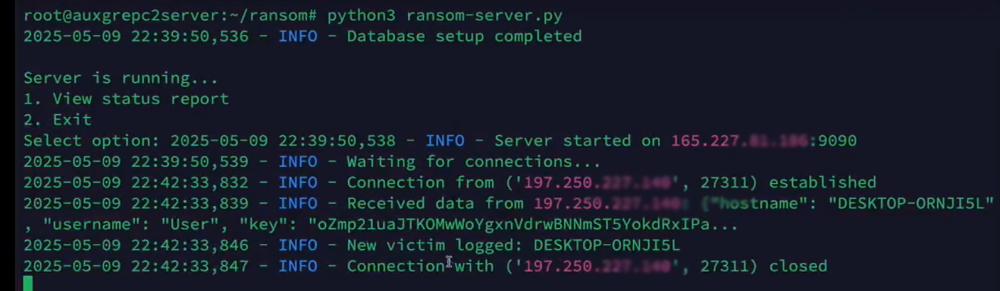
- The script downloads a Base64-encoded .NET assembly from another JPG file.
- This leads to ransomware payload execution, encrypting files undetected by traditional antivirus solutions.
- Attackers are also deploying RATs like LimeRAT, AgentTesla, and Remcos using this technique.
- Malware remains undetected using cryptors and steganography, avoiding signature-based detection.
- Threat actors exploit security software blind spots by embedding code within image pixel data instead of visible metadata.
Stay Protected:
- Use advanced email filters that scan embedded image content.
- Disable macro execution in Office documents by default.
- Maintaine regular, offline backups of vital files.
- Deploy behavior-based detection systems.
- Avoid downloads of images or files from untrusted or unknown sources.
What appears to be a harmless image could be a ticking cyber time bomb. As cybercriminals exploit the smallest vulnerabilities to carry out devastating attacks, it’s critical for users and organizations to move beyond outdated defenses and embrace AI-powered, behavior-driven cybersecurity solutions. Stay secure — because today, even a picture can be worth a thousand breaches.






