New Win-DoS Vulnerabilities Transform Windows Servers into DDoS Botnets
At DEF CON 33, researchers Yair and Shahak Morag from SafeBreach Labs unveiled a new class of denial-of-service (DoS) attacks called the “Win-DoS Epidemic.” They identified four new Windows DoS vulnerabilities and one zero-click distributed denial-of-service (DDoS) flaw, all categorized as “uncontrolled resource consumption.”

The vulnerabilities include:
- CVE-2025-26673 (CVSS 7.5): High-severity DoS in Windows LDAP.
- CVE-2025-32724 (CVSS 7.5): High-severity DoS in Windows LSASS.
- CVE-2025-49716 (CVSS 7.5): High-severity DoS in Windows Netlogon.
- CVE-2025-49722 (CVSS 5.7): Medium-severity DoS in Windows Print Spooler, requiring an authenticated attacker on an adjacent network.
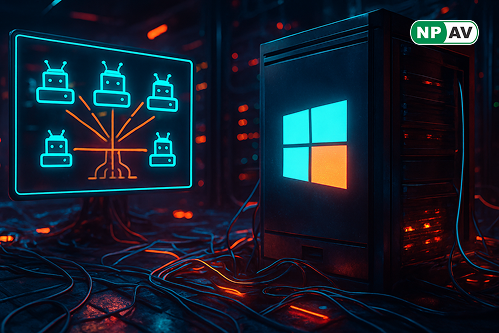

These vulnerabilities can crash any Windows endpoint or server, including critical Domain Controllers (DCs), potentially creating a massive DDoS botnet using public DCs.
A successful DoS attack on a DC can disrupt an entire organization, preventing user logins and access to resources. The researchers also introduced a novel DDoS technique, Win-DDoS, which exploits a flaw in the Windows LDAP client’s referral process, allowing attackers to redirect DCs to a victim server and repeatedly execute this redirection, effectively turning public DCs into a free, untraceable DDoS botnet.
Additionally, the researchers found vulnerabilities in the Remote Procedure Call (RPC) protocol, enabling attackers to crash Windows systems without authentication.






