PC Optimizer

Today PC's get cluttered with more damaging data, junk, and extra files than ever. This results in poor PC performance, frequent system crashes, slow Internet connections and worse. PC Optimizer makes your PC fast and stable also removes errors in your windows registry.
Features:
|
|
Faster System Speeds
PC Optimizer revives your PC to a state of optimal performance and stability. Makes your PC fast and stable also removes errors in your windows registry. |
|
|
Improved System Response Time.
PC Optimizer cleans the Registry for invalid information such as Invalid Fonts, Activex and COM Sections, invalid File Information, Auto-Run sections, DLL and Help sections for invalid entries. It reduces overall errors and improves efficiency. |
|
|
Smooth System Operation.
With its comprehensive suite of utilities and attractive interface, PC Optimizer makes it easy to regularly clean and optimize your system for better performance. |
|
|
Less Error Messages.
PC Optimizer is the easiest and most comprehensive way to keep your PC run smooth and error free. |
|
|
An Optimized Registry.Cleans invalid entries, scans and cleans your registry, cleans unwanted files on Disk. |
|
|
More Stable System.
It removes junk and obsolete files from your system. PC Optimizer takes backup and Restores With Backup. Restore tools helps to you restore registry. |
|
|
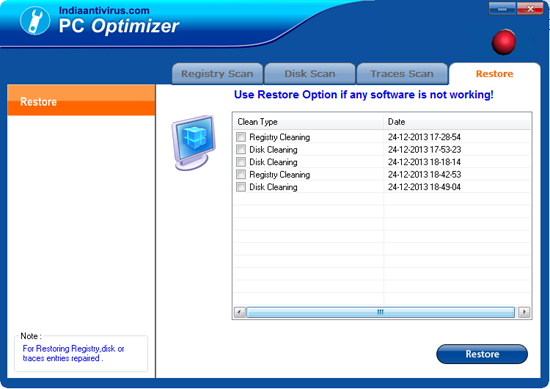
Restore
Restores previously cleaned items. Restore can undo the changes done earlier by restoring the backup. |
PC Optimizer - Used for the deleting unwanted Registry Entries.
It delete all the Registry Entries,Disk Entries,Trace Entries which unwanted.
Option:
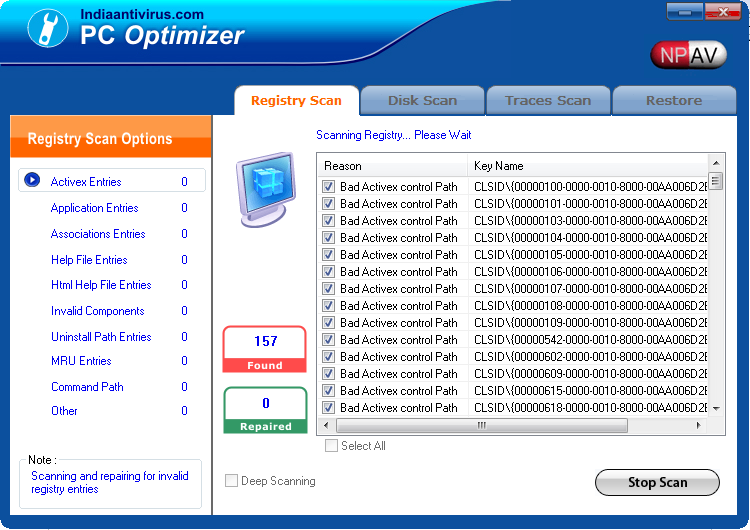
1. Registry Scan:
- Active x Entries:
Web add-ons,that are used extensively on the Internet.
- Application Entries:
Applications which open by the user.
- Association Entries:
If a program stops responding (or "hangs"), knowing which process
is associated with the program can help you troubleshoot the problem.
- Help File Entries:
The Help for this program was created in Windows Help format, which depends on a feature
that isn't included in this version of Windows .
- HTML Help File Entries:
The Help for this program was created in Windows HTML Help format, which depends on a
feature that isn't included in this version of Windows.
- Invalid Component:
If user enter the invalid key or any file which is store in the registry .
- Uninstall Path Entries:
User uninstall any software then there path should be deleted.
- MRU Entries:
User Log-in and Log-off entries should be deleted.
- Command Path:
All users network path which are not connected and invalid should be deleted.
- Start Scan:
If you start the scan then click on these button.
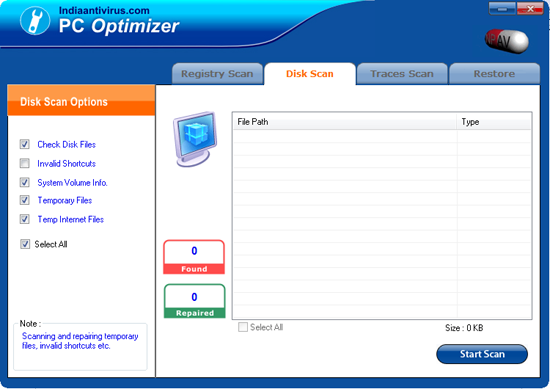
2. Disk Scan:
- Check Disk Files:
User any unwanted files and there reg entries should be deleted .
- Invalid Shortcut:
All invalid shortcut should be deleted.
- System Volume Info:
When user use any file backup is in the System Vol Info is deleted.
- Temporary Files:
When user used the file also created in Temporary file is to be deleted.
- Temporary Internet Files:
User using the internet file are created in this folder.
- Start Scan:
If you start the scan then click on these button.
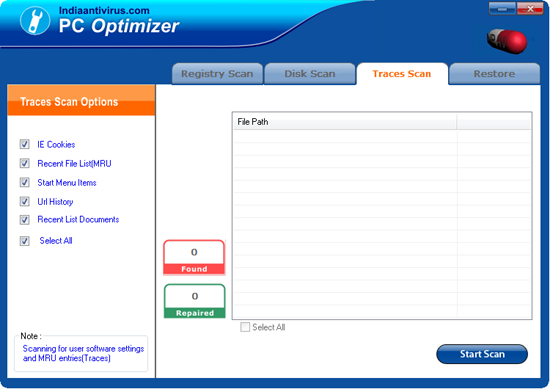
3.Trace Scan:
- IE Cookies:
Internet Explorer favorites are links to websites that you visit frequently .
- Recent File List:
Recently open file by the user.
- Start Menu Items:
User start-up item should be deleted.
- URL History:
While using Internet all the URL history should be deleted.
- Recent List Document:
Clear all the start-up menu and the task-bar entries.
- Start Scan:
If you start the scan then click on these button.
4. Restore:
- Restore:
User want there old backup it restore form these Restore Button.