Phishing
-
Read moreA sophisticated phishing attack uses Facebook’s URL redirect service to trick users into entering login credentials on fake pages, stealing emails, phone numbers, and passwords.
-
Read moreSpamGPT is a dark web “spam-as-a-service” platform using AI to automate large-scale phishing campaigns. Learn how KaliGPT and SMTP cracking training empower cybercriminals.
-
Read moreCybercriminals abused compromised AWS credentials to hijack Amazon SES, sending 50,000+ phishing emails daily by bypassing sandbox limits. Learn how to detect and prevent SES abuse.
-
Read moreA sophisticated OneDrive spearphishing campaign targets corporate executives with fake HR emails and Microsoft Office 365 login pages to steal credentials. Learn how to recognize and prevent this threat.
-
Read moreDiscover how cybercriminals are exploiting brokerage accounts in sophisticated ‘ramp and dump’ schemes using mobile phishing tactics. Learn about the risks and how to protect yourself.
-
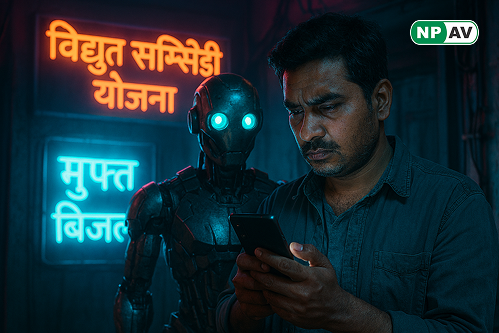
Read moreA new Android phishing campaign is deceiving Indian users by posing as the PM Surya Ghar: Muft Bijli Yojana. Learn how attackers exploit this scheme to install malware and steal sensitive banking information.
-
Read moreDiscover how artificial intelligence is reshaping phishing tactics in cybercrime. Learn about AI-driven scams, deepfake technology, and the exploitation of messaging platforms.
-
Read moreGoogle's Salesforce instance was compromised by the ShinyHunters group using voice phishing tactics. Learn about the breach and the exposed records.
-
Read moreDiscover how phishing scams are targeting users through WhatsApp messages, including a recent HDFC Bank impersonation attempt. Learn how to protect yourself with FraudProtector.Net.
-
Read moreA series of data breaches linked to the ShinyHunters group has affected major companies like Qantas and LVMH. Learn how voice phishing techniques compromised Salesforce CRM systems and the implications for data security.