16 Chrome Extensions Hacked, Exposing Over 600,000 Users to Data Theft

A large-scale phishing attack has compromised 16 popular Chrome browser extensions, exposing over 600,000 users to data theft and credential breaches. The campaign exploited legitimate extension publishers, injecting malicious code into their products to steal sensitive information such as cookies and access tokens.
- 16 Chrome Extensions, including popular ones like "AI Assistant - ChatGPT and Gemini for Chrome," "GPT 4 Summary with OpenAI," and "Reader Mode," were compromised, exposing sensitive user data.
- The attackers targeted browser extension publishers with phishing campaigns to gain access to their accounts and insert malicious code.
- Extensions such as "Rewards Search Automator" and "Earny - Up to 20% Cash Back" were used to exfiltrate user credentials and identity tokens, particularly from Facebook business accounts.
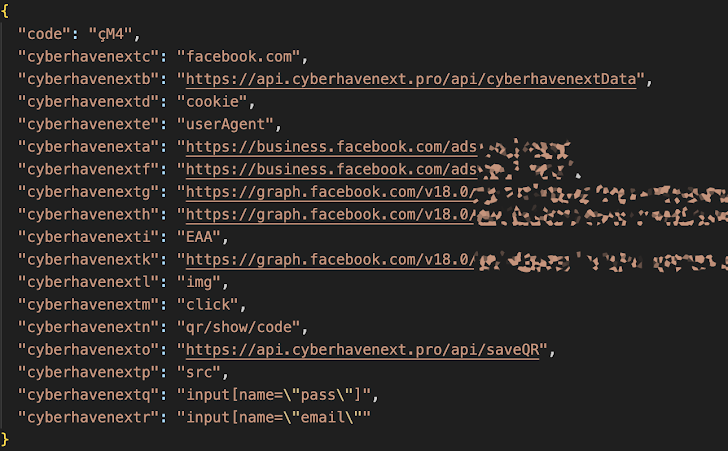
- Malicious versions of extensions communicated with external Command-and-Control (C&C) servers, such as domains like "cyberhavenext[.]pro."
- Attackers utilized a phishing email posing as Google Chrome Web Store Developer Support, tricking victims into granting permissions to a fake OAuth application, "Privacy Policy Extension."
- Other impacted extensions include "Vindoz Flex Video Recorder," "TinaMind AI Assistant," "Bookmark Favicon Changer," and "VPNCity."
- The attack campaign may have been ongoing since at least April 2023, with some domains registered as far back as 2021.
- Even after removal from the Chrome Web Store, compromised extensions can still pose risks if installed on user devices.
This incident underscores the vulnerabilities inherent in browser extensions, which often have extensive access to sensitive user data. Organizations must proactively manage the extensions installed on their endpoints and regularly review permissions. Using advanced cybersecurity solutions like Net Protector Endpoint Security can help detect malicious activity and safeguard sensitive information from such sophisticated threats. Stay alert, verify extension sources, and adopt robust protection measures to mitigate risks.






