Critical Vulnerability in TP-Link Gaming Router Exposes Users to Remote Code Attacks

In a concerning development for cybersecurity, a maximum-severity security flaw has been discovered in the TP-Link Archer C5400X gaming router, potentially allowing remote code execution on vulnerable devices. This vulnerability, tracked as CVE-2024-5035, has earned a CVSS score of 10.0, indicating its critical nature.
The Scope of the Vulnerability
The flaw affects all versions of the router firmware up to and including 1_1.1.6. TP-Link has addressed the issue in firmware version 1_1.1.7, released on May 24, 2024. German cybersecurity firm ONEKEY, which uncovered the vulnerability, has highlighted the severe risk posed by this flaw. If exploited, remote unauthenticated attackers can execute arbitrary commands on the device with elevated privileges.
Technical Details
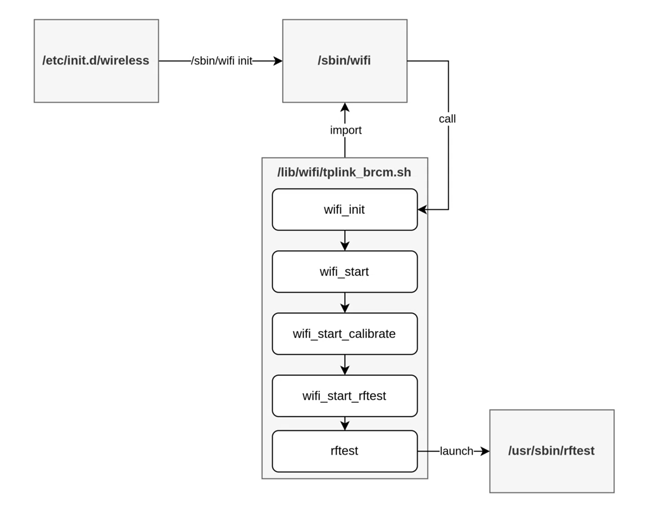
The vulnerability stems from a binary related to radio frequency testing called "rftest," which launches at startup and exposes a network listener on TCP ports 8888, 8889, and 8890. This setup allows remote unauthenticated attackers to achieve code execution by sending specially crafted requests.
ONEKEY's report reveals that the network service is intended to only accept commands beginning with "wl" or "nvram get." However, this restriction can be easily bypassed by injecting a command after shell meta-characters such as ;, &, or |. For example, a command like "wl;id;" can be used to bypass the restriction and execute arbitrary commands.
The Fix and Recommendations
TP-Link's patch in version 1_1.1.7 Build 20240510 mitigates the vulnerability by discarding any command containing these special characters. This update is crucial for users to prevent potential exploitation.
ONEKEY's analysis suggests that the vulnerability arose from the need to quickly provide a wireless device configuration API, leading to an insecure implementation that exposed a limited shell over the network.
Broader Implications
This disclosure comes shortly after the revelation of other security flaws in networking devices, including Delta Electronics DVW W02W2 industrial Ethernet routers (CVE-2024-3871) and Ligowave networking gear (CVE-2024-4999). Unlike the TP-Link flaw, these vulnerabilities remain unpatched as the devices are no longer actively maintained. This highlights the ongoing challenges in securing older or less frequently updated hardware.
Given the critical nature of this vulnerability, TP-Link Archer C5400X users should immediately update their firmware to version 1_1.1.7 or later. Additionally, users should take the following steps to enhance their network security.
Source: The hackernews
Regular Firmware Updates: Always keep device firmware up-to-date to benefit from the latest security patches.
Restrict Network Access: Limit exposure of administration interfaces to reduce the potential for exploitation.
Monitor Network Activity: Regularly review network logs and monitor for unusual activity that could indicate a security breach.
As cyber threats continue to evolve, staying informed and proactive about cybersecurity is essential. The TP-Link gaming router vulnerability serves as a stark reminder of the importance of regular updates and vigilant security practices to safeguard against potential attacks.






