Cyber criminals are sending malicious pdfs tricking users to believe it is a purchase order.
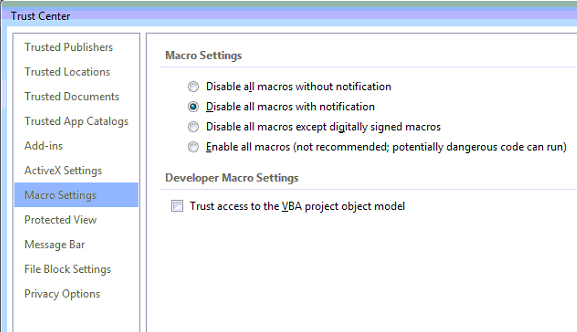
Hackers are sending various phishing emails that portrays itself as a genuine order.
Phishing emails have always been a preferred weapon used by hackers to launch cyber attacks. Recently a new phishing email has surfaced that contains a fake order detail with addresses and attached pdf. The pdf attached to the email is reported to be malicious.
The screenshot of the email reported is shared below.
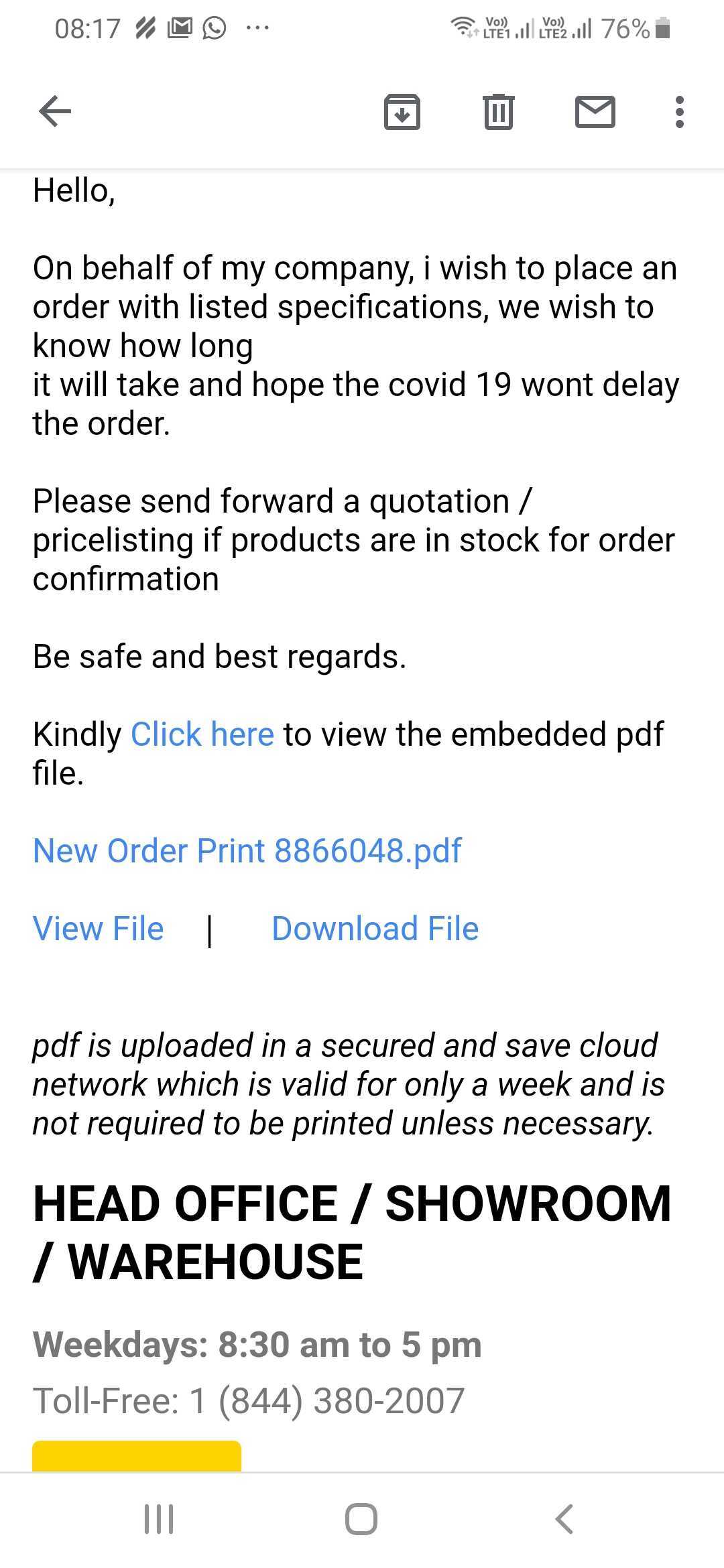
Hackers have always used various methods to make the phishing emails look genuine. In the above mentioned case the phishing mail contains the reference of COVID-19 virus and the latency it can cause. If the target gets lured by the mail and downloads the attachment it can cause various malicious threats. The embedded file can contain malware backdoor, bugs or any other malicious exe.
NPAV recommends users to never fall victim to such phishing attacks and never download any attached file with such emails or messages. Downloading such files can cause huge menace to your system and devices.
Use NPAV and join us on a mission to secure the cyber world.






