Latest Version of Hijack Loader Malware Utilizes Process Hollowing and UAC Bypass

In the ever-evolving landscape of cybersecurity threats, the emergence of a newer version of the malware loader, Hijack Loader, has sent ripples across the industry. This updated iteration comes equipped with a sophisticated arsenal of anti-analysis techniques, designed to cloak its activities and evade detection for prolonged periods.
According to Zscaler ThreatLabz researcher Muhammed Irfan V A, these enhancements aim to enhance the malware's stealthiness, making it increasingly challenging for security software to identify and neutralize. The Hijack Loader now boasts modules tailored to bypass Windows Defender Antivirus, circumvent User Account Control (UAC), evade inline API hooking, and employ process hollowing, among other techniques.
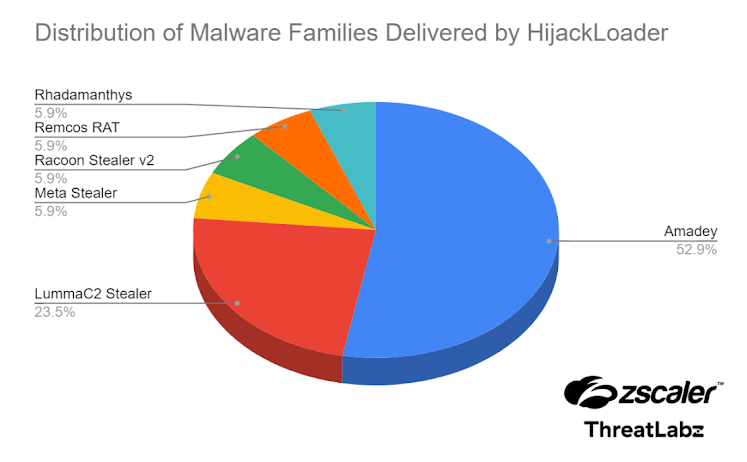
Originally documented by cybersecurity experts in September 2023, Hijack Loader has since evolved into a conduit for delivering various malware families, including Amadey, Lumma Stealer, Meta Stealer, and Remcos RAT, to name a few. However, what sets this latest version apart is its utilization of a novel technique involving the decryption and parsing of a PNG image to load the next-stage payload. This method, first detailed in connection with a campaign targeting Ukrainian entities, adds another layer of complexity to the malware's operation.
The loader's sophistication doesn't end there. Recent artifacts detected in the wild reveal the incorporation of seven new modules, enabling the creation of new processes, UAC bypass, and the addition of Windows Defender Antivirus exclusion via PowerShell commands. Additionally, the Hijack Loader leverages the Heaven's Gate technique to circumvent user mode hooks, further enhancing its stealth capabilities.
Among the malware families most commonly delivered by Hijack Loader, Amadey stands out, with its second-stage payload loaded via an embedded or downloaded PNG image. As Hijack Loader continues to evolve, integrating new modules and enhancing its capabilities, the challenge of combating its stealthy operations grows ever more daunting.
This development occurs against the backdrop of malware campaigns distributing various loader families like DarkGate and GuLoader, underscoring the persistent threat posed by cybercriminals. Moreover, the emergence of information stealers like TesseractStealer, distributed by ViperSoftX, further highlights the need for heightened vigilance in the face of evolving cyber threats.
In the ongoing battle against cyber adversaries, staying informed and proactive is paramount. By understanding the tactics and techniques employed by malware like Hijack Loader, organizations and individuals alike can better protect themselves against the ever-present threat of cyber attacks.






